Setup advanced SSO for multi-tenancy
Frontegg's Advanced SSO for Multi-tenancy simplifies user access across multiple applications under a single domain. It allows multiple SSO connections within the same domain, segregating data access by team. Each team can configure SSO for specific tenants, enhancing security and streamlining the user experience.
Frontegg enforces domain validation for SSO connections initiated via the self-service portal to prevent domain abuse and ensure each domain is uniquely tied to an account and environment. With SSO multi-tenancy enabled, customers can use the same domain for multiple SSO configurations across tenants, granting data access to specific users securely.
Prerequisites
Prerequisites
@frontegg/react@5.0.45
@frontegg/nextjs@7.0.14
@frontegg/angular@5.35.0
@frontegg/vue@2.0.40
Configuring SSO for multi-tenancy
To configure SSO for multi-tenancy, go to [ENVIRONMENT] → Authentication → SSO → Service provider → Multitenancy SSO.
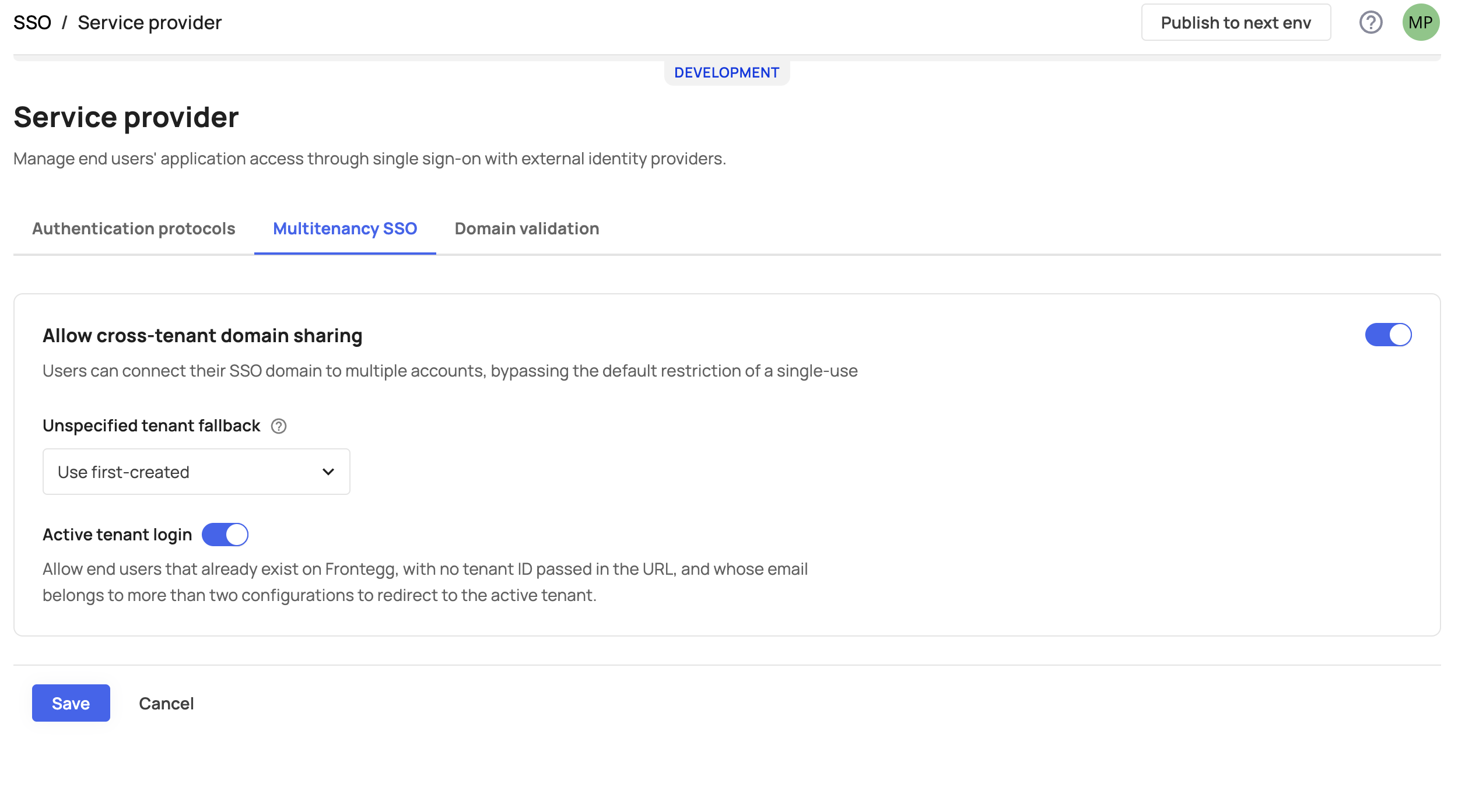
Allow cross tenant domain sharing - note that this field is optional and is disabled by default.
Block the login - this field will block non existing users whose domain is associated to multiple accounts from proceeding with the SSO login, unless tenantId={{tenantId}} will be passed in the search params of the login route. In this case, the user will be prompted to use the default authentication method (i.e., password / passwordless).
Use first-created - this option will redirect a non-existing user whose email domain is used in several SSO connections and isn't passing tenantId={{tenantId}} in the login, to the tenant on which the first SSO configuration was created and is therefore linked to the user domain.
Active tenant login - A configuration bundled with one of the following options: Block the login / Use first-created which redirects an existing user (whose email domain is used in more than one SSO configuration) to the user's currently active account.
Redirecting users with multiple SSO configurations
Frontegg login initiated flow - when a user domain is associated with multiple SSO configurations across multiple accounts, the user will need to pass their
tenantIdin the login URL so Frontegg can redirect them to the SSO endpoint associated with that account. If a user exists but does not pass theirtenantId— Frontegg will default to the account redirect where the user's first SSO configuration was created or will block login via SSO.IdP initiated flow - when a user domain is associated with multiple SSO configurations across multiple accounts, the user will get redirected to the account where the SSO connection they're logging through is applied.
The following example URLs contain the tenantId identifier as it should be passed from Frontegg login:
// Hosted login
https://[your-frontegg-workspace-url]/oauth/account/login?tenantId={{tenantId}}
// Embedded Login
https://[your-application-url]/account/login?tenantId={{tenantId}}