Configure OpenID Connect on your environment
OpenID Connect protocol is an identity layer on top of the OAuth 2.0 protocol. By configuring OpenID, you can allow users to sign in with their OpenID credentials and pass your users' authenticated sessions back to your system so they can be used across multiple applications for authentication.
To configure your environment as Service Provider and allow users to sign-in via OpenID, go to [ENVIRONMENT] → Authentication → SSO → Service Provider → Authentication protocols. If you do not see OpenID under this page, please make sure it is enabled in the builder and published to the environment.

OpenID enablement
OpenID enablement
Setting a custom domain after going live, especially with active SSO connections, can be challenging. We recommend planning ahead and setting custom domains early to avoid cookie issues and enhance your brand. This applies to both Hosted and Embedded Frontegg customers. [Learn more about Custom Domains.]
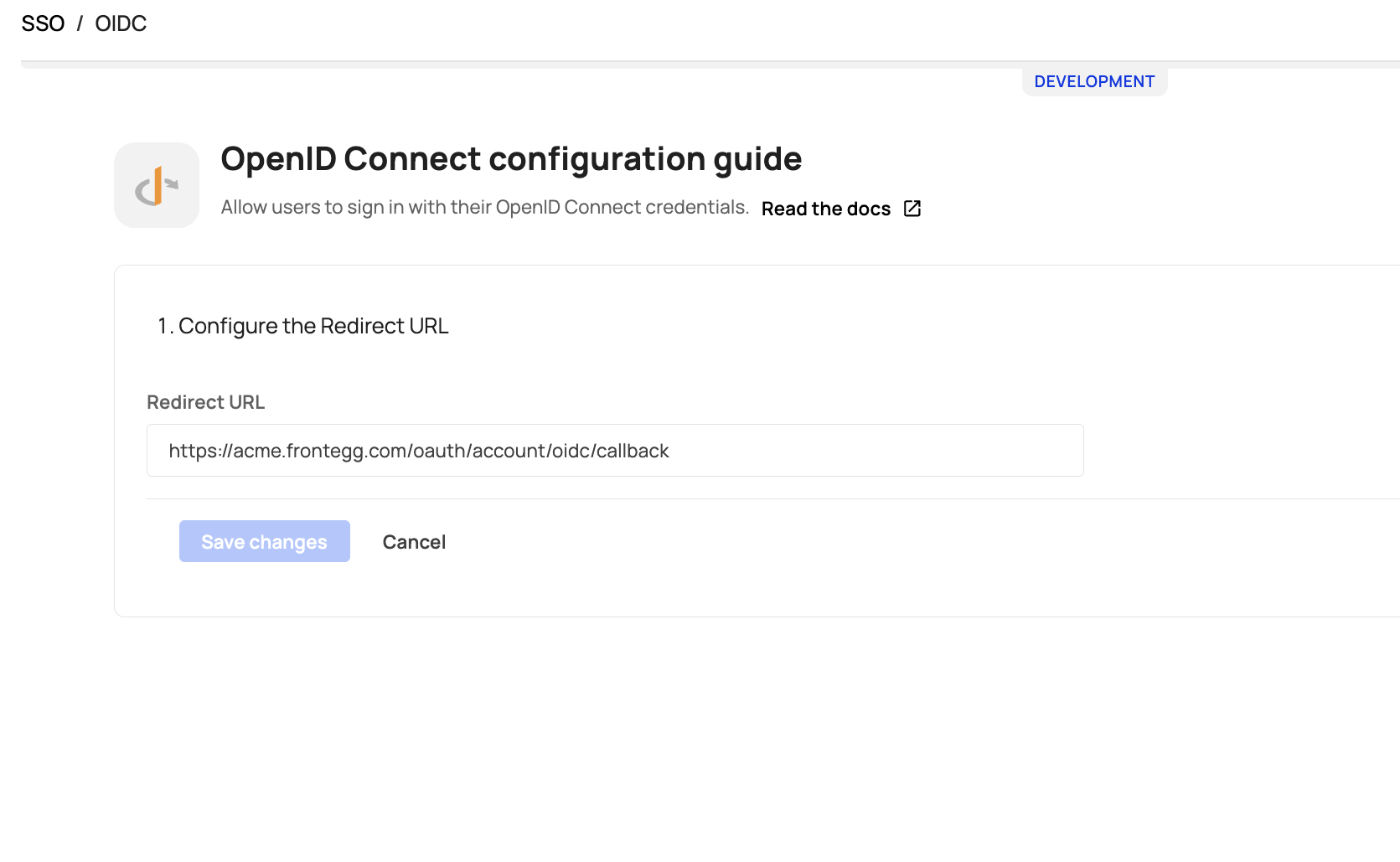
Add a redirect URL
After clicking the OpenID Manage button, insert your redirect URL and save the changes. If you are using the Hosted login method, the redirect URL should be:https://[your-frontegg-domain].frontegg.com/oauth/account/oidc/callback.
If you are using the Embedded Login method, the redirect URL should be:https://[your-application-url]/account/oidc/callback, for example: http://localhost:3000/account/oidc/callback.
Allow your customers to add their IdP connection or apply it for them
After configuring OpenID in the Frontegg portal, you can allow your end users to apply their own SSO connection or apply the connection details from their IdP for them (via your [ENVIRONMENT] ➜ Management → Accounts → [ACCOUNT] → SSO tab ➜ Configurations).
Enable SSO tab for the self-service (admin portal)
Enable the SSO tab for your users in the Workspace area of the portal. Subsequently, your users can follow the instructions to add their IdP connection as per the instructions [here].

Apply an SSO connection from your environment's management page
To apply an SSO connection on your customers' behalf, go to your Management → Accounts → [ACCOUNT] → SSO tab ➜ Configurations, and click 'add new'. Alternatively, you can also perform this action via API.

Users group-to-role mapping
Often, end users logging in via SSO to your application need their application roles mapped to the groups assigned to them on the IdP side. By default, all users logging in through a specific SSO configuration receive the default role. If they belong to a group mapped to an additional role, they will receive that role in addition to the default SSO role.
For OpenID, there is no option to map roles to groups from the self-service UI (Admin portal). It can be applied only via APIs or the Management page in the Frontegg portal.
Groups scope
Groups scope
Note that Frontegg uses openid, profile, email in the requested scopes from external IdPs. Some IdPs may require additional scopes for passing user groups back to the service provider (Frontegg).