Getting started with entitlements
Entitlements in Frontegg offers a powerful way to manage and control feature availability within your application. It allows you to define which features are accessible to different users, enabling you to tailor the user experience, support feature rollouts, and streamline access management. By leveraging Entitlements, you can ensure a smooth and flexible approach to delivering features while aligning with your product and business goals.
Entitlements core concepts
Entitlements enables user access within your application by assigning specific roles, permissions, feature access, and more. To help you understand how the various entitlement features work together, here’s a quick overview that explains their relationships:
Specific functionalities within your application that can be enabled or restricted for users via plans or feature flags
Subscription tiers or packages that define access to features and functionalities based on a user's plan.
A toggle that controls the rollout and availability of features to users for testing or gradual deployment.
Main use cases for entitlements' management:
Our Entitlements engine is here to allow you create:
- Control access to features based on user entitlements: Ensure users only access features aligned with their subscriptions or permissions.
- Manage subscription plans effectively: Enforce tiered access to features based on the user's specific subscription plan.
- Implement feature flagging: Control the visibility of features for different user segments, enabling A/B testing and phased rollouts.
Entitlements vs. traditional RBAC
Role-Based Access Control (RBAC) is a good starting point for managing who has access to what. But to really unlock the power of access control, you need Entitlements.
Think of Entitlements as fine-grained access control. It lets you personalize what each user can see and do in your application, down to the individual feature level. This not only improves the user experience but also opens up new opportunities for monetization. You can offer different subscription tiers with varying levels of access, or even charge for individual features.
In a nutshell, Entitlements helps you:
- Personalize: Tailor user experiences to individual needs and preferences.
- Monetize: Create flexible pricing plans and increase revenue.
- Secure: Maintain strong security with granular access control.
- Stay Agile: Quickly adapt to changing market needs and customer demands.
By moving beyond basic RBAC and embracing Entitlements, SaaS platforms can deliver a more tailored, valuable, and secure experience for their users.
How it works?
Using the entitlements agent
Entitlements boil down to a simple yes-or-no question: Does this user have access to this feature? Here's an overview of how you can make it work
To make Entitlements work its magic, you'll need to install the Entitlements Agent. This agent acts like a bridge between your application and Frontegg's Entitlements system. Here's how it works:
- Dockerized for reliability: The agent is built using Docker, ensuring it runs smoothly and consistently in various environments.
- Real-time updates: The agent constantly communicates with Frontegg’s Cloud, ensuring that your application has the latest information about which users have access to which features.
- Optimal latency: The agent operates with all the necessary data for decision-making, and invoking it within your network environment ensures the lowest possible latency.
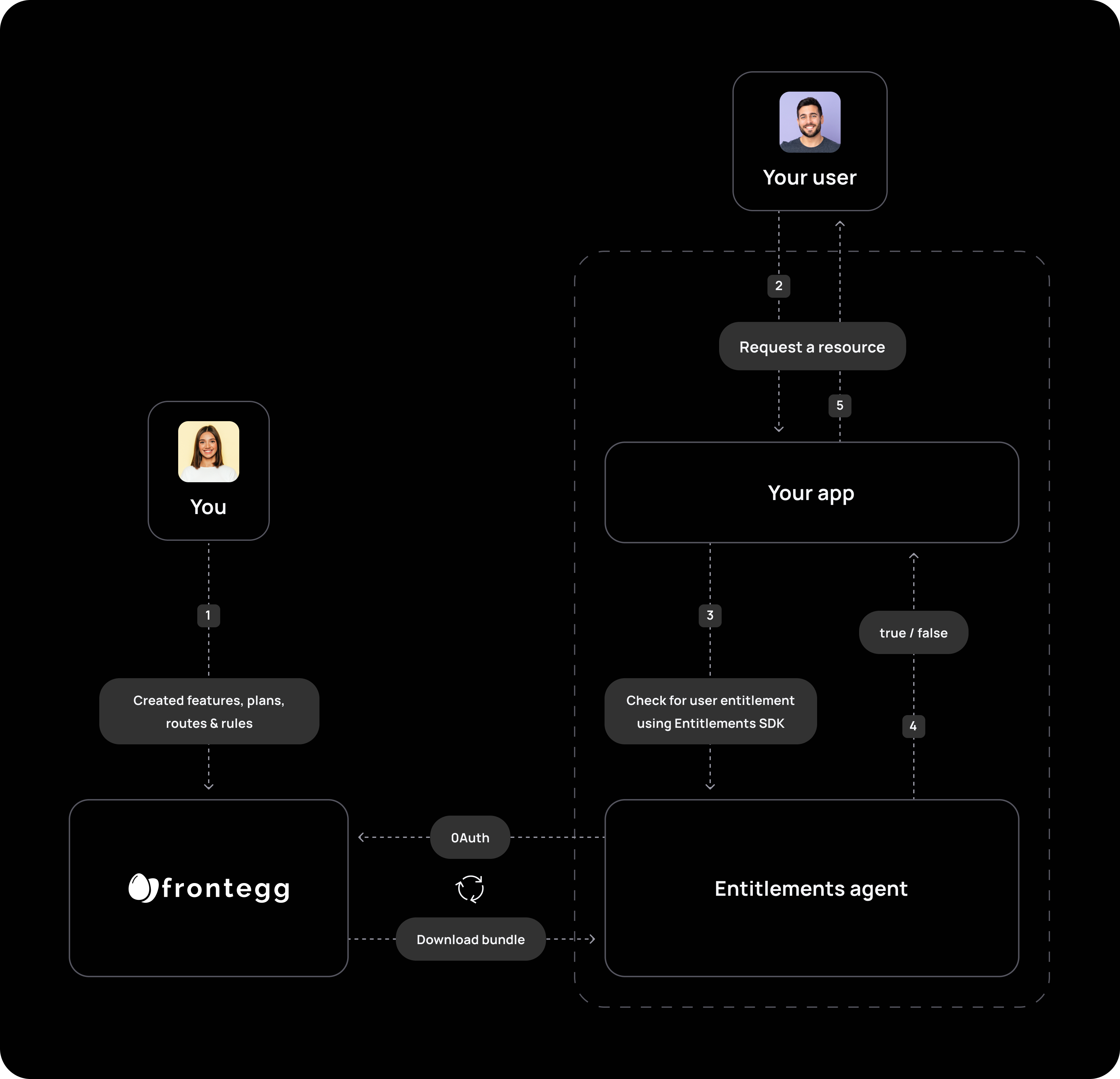
You can query the Entitlements agent with Node.js SDK OOTB, or work with your own framework via HTTP call. Learn more about it here.
Another way to work with Entitlements is using this backend SDK (find more information in this repository) - it does not require setting up the agent.
However, it doesn't unlock the full potential of Frontegg's Entitlements Engine. For more advanced features, such as "API access control", you'll need to leverage the Entitlements Agent.
This agent acts as a bridge between your application and Frontegg, providing real-time entitlement updates and enabling fine-grained protection of your APIs.
Enforcing entitlement in the UI
Our frontend SDK empowers you to seamlessly integrate entitlement protection directly into your user interface. By utilizing the SDK, you can easily control access to specific features or content based on user access.