Flows overview
Frontegg Flows is a powerful tool designed to manage complex user journeys across multiple platforms and applications. With an intuitive UI, it allows you to customize native user flows within your app seamlessly.
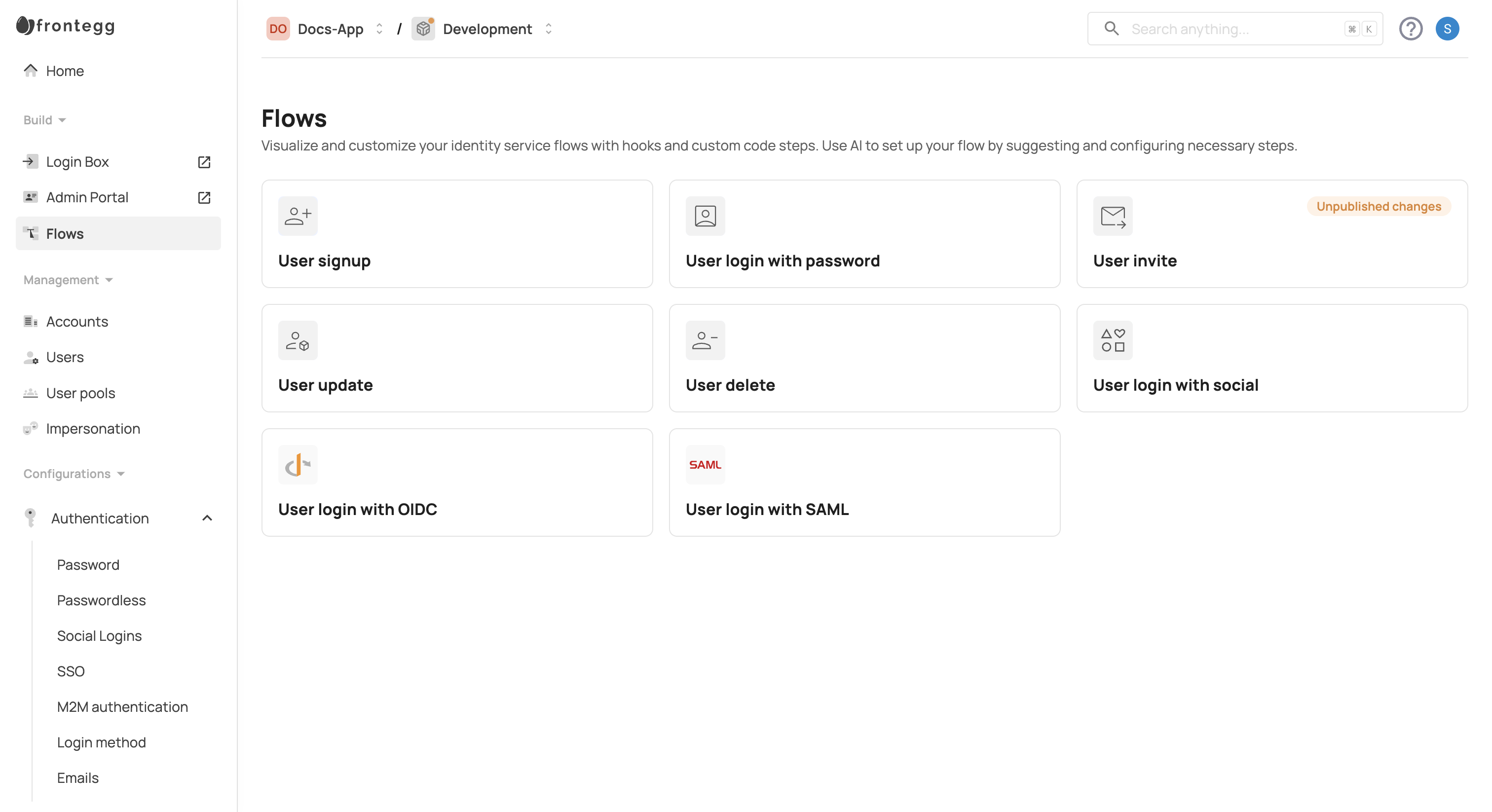
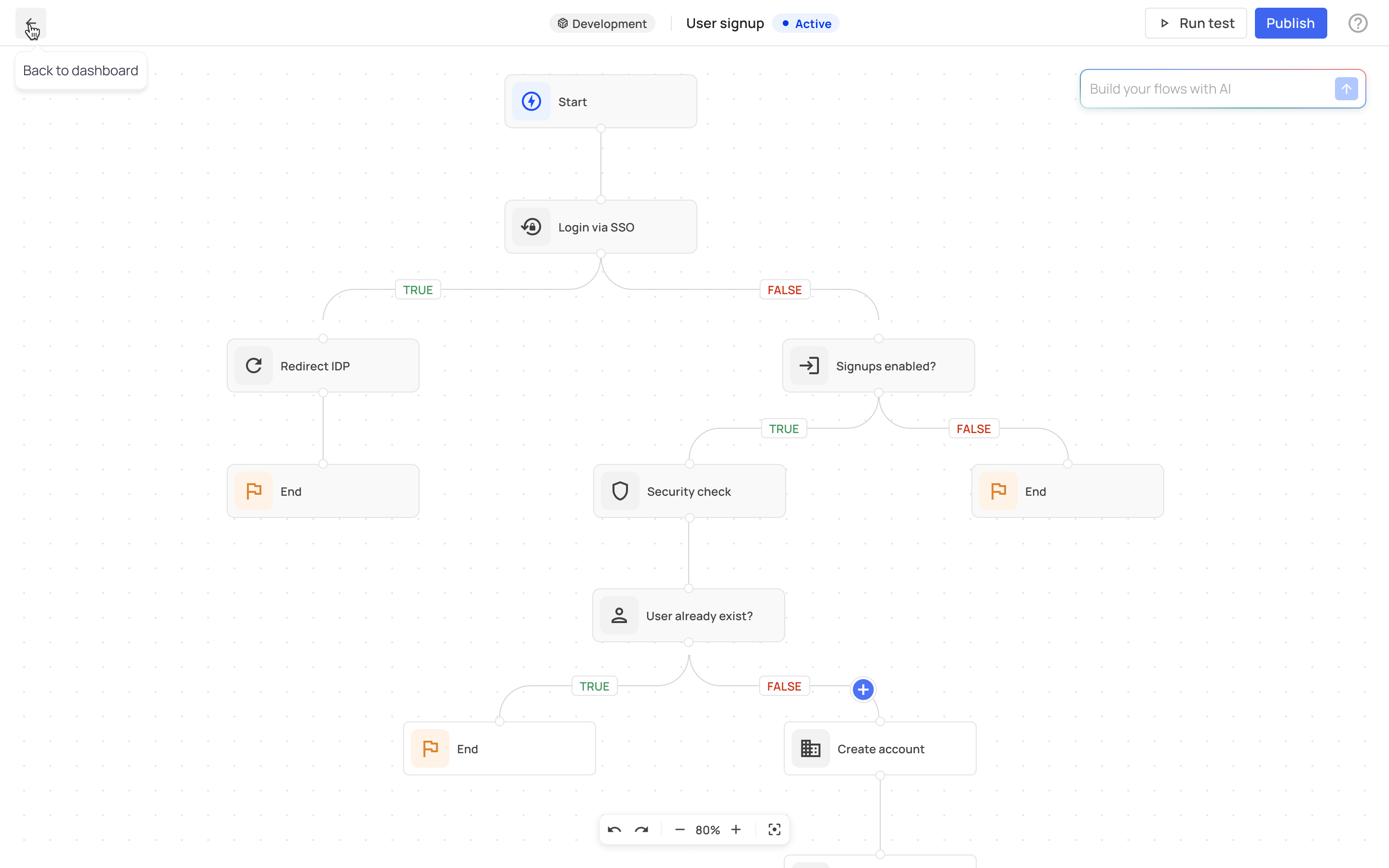
When you access the Flows dashboard, you can use our no-code solution to add steps to the user lifecycle via the '+' signs at strategic junctions. Customize your flows manually by adding webhooks, prehooks, and sub-flows, or leverage our integrated Natural Language Processing (NLP) AI technology to describe the flow steps, and it will generate a customized flow for you.
The flows provide a clear overview of the different steps and the points where the user journey diverges:
Benefits
Frontegg Flows offers multiple benefits for user journey orchestration, including flexibility, ease of creation, and advanced technology:
- Creating unlimited sub-flows: Sub-flows, which are mini-flows triggered by user activity, can be created and reused within multiple flows. Learn more about sub-flows in the configuration section.
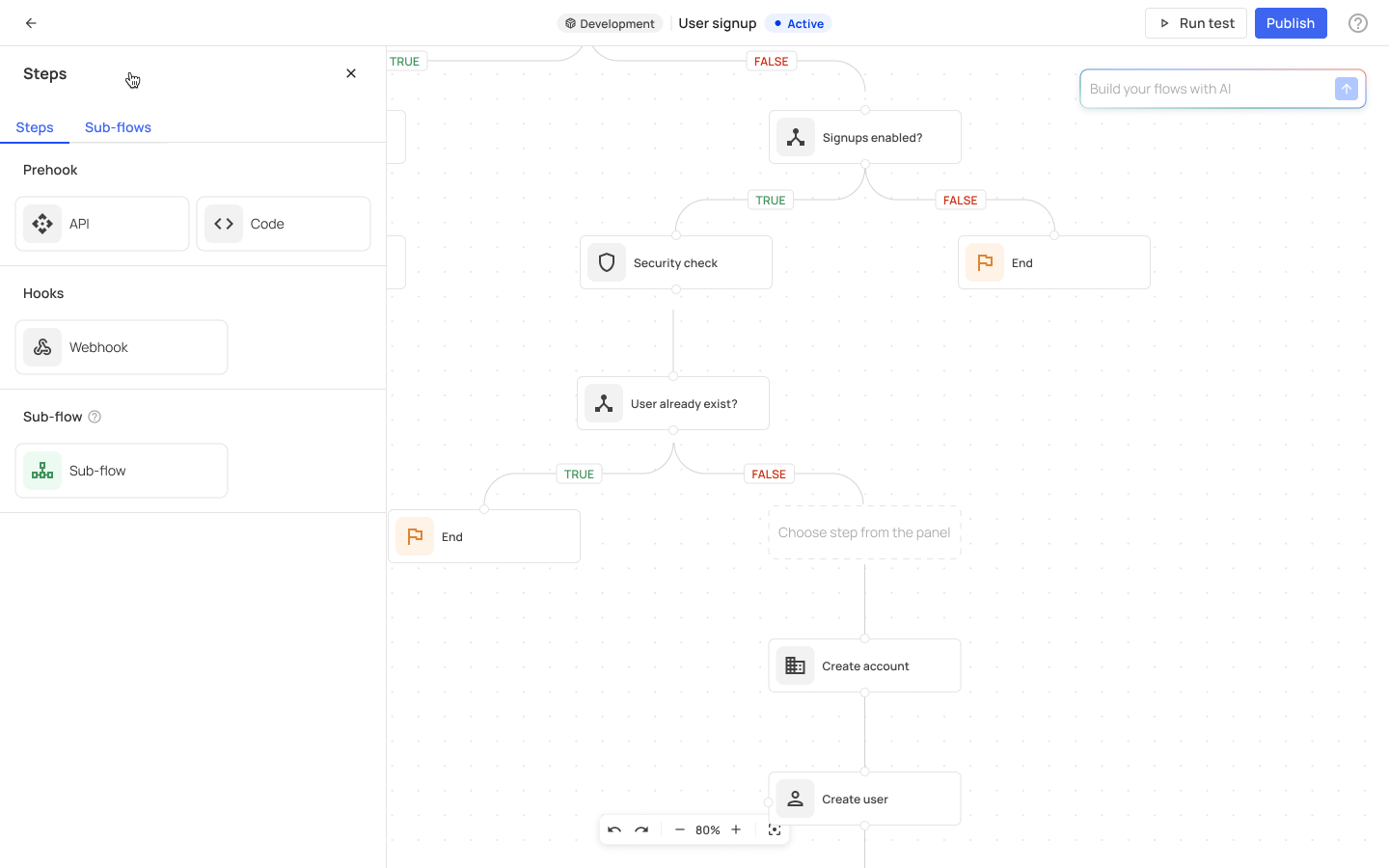
AI innovation: The AI capability reduces the time and expertise needed to set up flows, making it accessible for users without deep programming knowledge. It includes a review and edit function for fine-tuning the generated flows. Input a statement like "When a user signs up, verify their email address and add them to the 'New Users' group," and the AI will construct the corresponding flow with the necessary triggers, actions, and conditions.
Security and compliance: Frontegg Flows empowers you to implement advanced security measures within user journeys, ensuring protection and regulatory compliance, such as with GDPR. You can configure access controls based on roles, enforce step-up authentication for sensitive actions, and enable MFA dynamically, such as for first-time logins or high-security operations. Location-based restrictions can block logins from unauthorized regions or prompt users with region-specific terms and conditions. Flows also help mitigate threats by detecting anomalous behavior—like unfamiliar devices or locations—and triggering additional authentication steps. These features let you safeguard your application while meeting evolving security and compliance requirements.
Use cases
Harness the power of flows to create tailored user journeys that align with your business needs. Here are some examples showcasing their flexibility:
Customized user journeys: Differentiate between new user sign-ups and regular logins. For instance, create distinct flows for onboarding versus returning users to streamline their experience.
Restricted sign-up origins: Allow sign-ups only from specific origins, such as AWS users or designated user pools, while blocking sign-ups from unauthorized sources.
New user registration: Facilitate first-time registration with multi-step verification. Users provide an email address, complete verification via a one-time password (OTP) or magic link, and finalize the process with biometric validation, such as fingerprint or facial recognition.
Conditional multi-factor authentication (MFA): Enforce MFA selectively. For example, require MFA only during a user's first login or trigger it based on key milestones within the application. Avoid unnecessary disruptions by skipping MFA for routine activities.
A/B testing for identity verification: Distribute users across two identity verification providers to compare performance metrics, such as conversion rates, and determine the most effective solution.
Location-based terms and conditions: Adapt user journeys based on geographical location. For example, display GDPR compliance terms during registration or login for users in Europe while bypassing it for others.
Post-login security checks: Implement workflows to ensure account integrity after login. This can include reviewing recent activity, verifying changes to security settings, or confirming newly added devices.
Anomaly-triggered step-up authentication: Detect unusual behaviors, such as logins from new devices or locations, and trigger additional authentication steps to verify the user's identity before granting access.