What are webhooks?
Frontegg webhooks enable you to automate workflows by triggering specific actions when events occur on Frontegg's servers. This powerful feature allows seamless integration with your existing systems and enhances your application's responsiveness.
Webhook use cases
By leveraging Frontegg webhooks, you can streamline operations, improve user interactions with your app, and control and direct your users' journey in a way that fits your business needs.
Here are some examples of how you can utilize Frontegg webhooks:
- Automating user registration: Automatically register a user in your internal database when they receive an invitation to join your application. This ensures that your records are always up-to-date without the need to manually log in new users.
- Marketing engagement: Send a personalized marketing email to users immediately after their first login. This can help welcome new users and introduce them to your app's features, thereby improving user engagement and retention.
- Transactional workflow generation: Create complex transactional workflows based on user login activities. For instance, you can trigger security checks, log user activity, or update user status in real time, enhancing both security and user experience.
Frontegg webhook IPs
Frontegg webhook IPs
Note the following list of Frontegg webhook IPs:
- EU IPs: 99.81.198.187
54.216.181.43
52.209.54.22 - US IPs: 23.21.59.58
54.152.159.125
3.220.173.9
Configuring webhooks
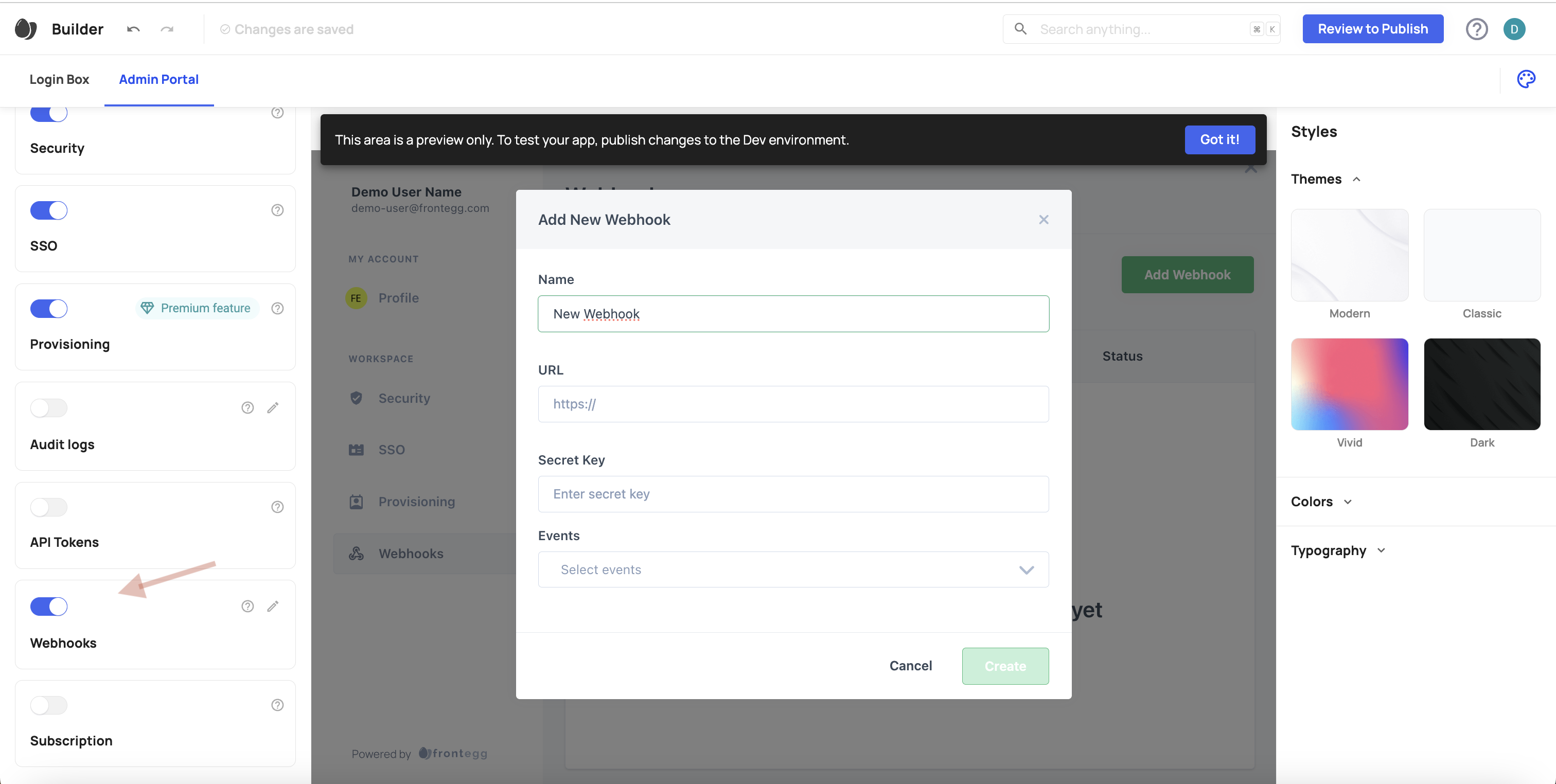
To create a new webhook connection, head over to your portal and choose [ENVIRONMENT] ➜ Integrations. The page lists all your webhooks and third-party integrations and allows you to create a new one.
Step 1: Create a webhook connection
Click the Connect button next to Webhooks. Fill in the webhook details for the display name and choose the events you want to subscribe to.
Step 2: Enter the URL address
Enter a valid URL to which you will receive the webhook data. The URL acts as the address where Frontegg sends a JSON message when the assigned event occurs. Only once you add a valid address can you test the webhook.
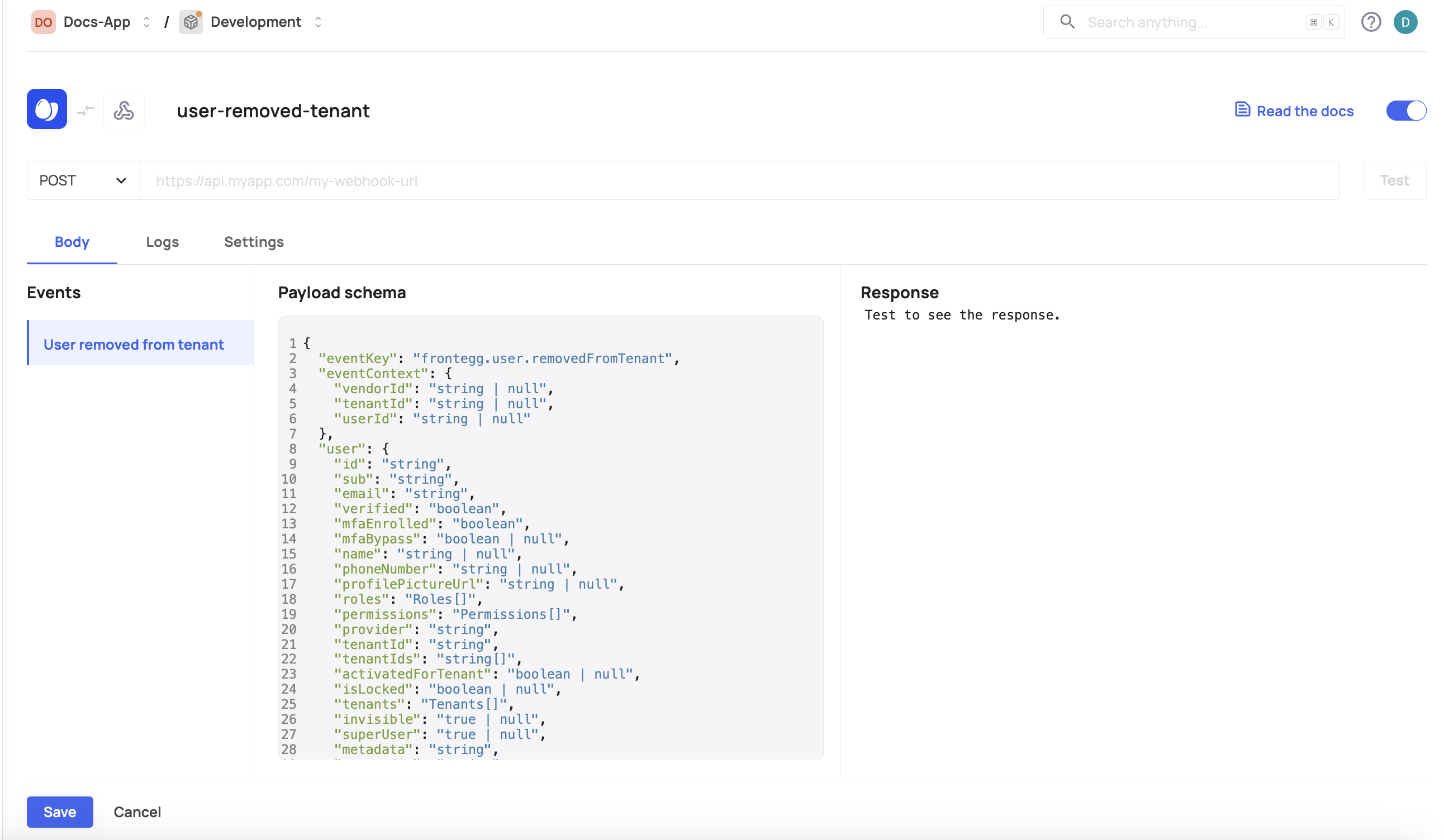
Step 3: Test your webhook request
Press the Test button to check that your webhook is working. For the test to succeed, ensure that your URL endpoint is up and running and returns a 200 response to the webhook request.
Webhook response
Webhook response
Note that any 2XX response will be registered as success, while 4XX responses will be registered as failure. The response body can remain empty.
Set a webhook secret key
We strongly recommend protecting your webhooks by setting a Secret Key for each webhook connection you create.
Go to your webhook's Settings tab and under the Secret key field, enter your desired value. Frontegg will generate a header called x-webhook-secret and will sign the webhook request with that secret value.
To verify the hook's signature using the x-webhook-secret header, you should use a method from your backend library. For Node.js, you can use the following function:
jwt.verify(<x-webhook-secret-value>, <the secret in the dashboard on hook settings>)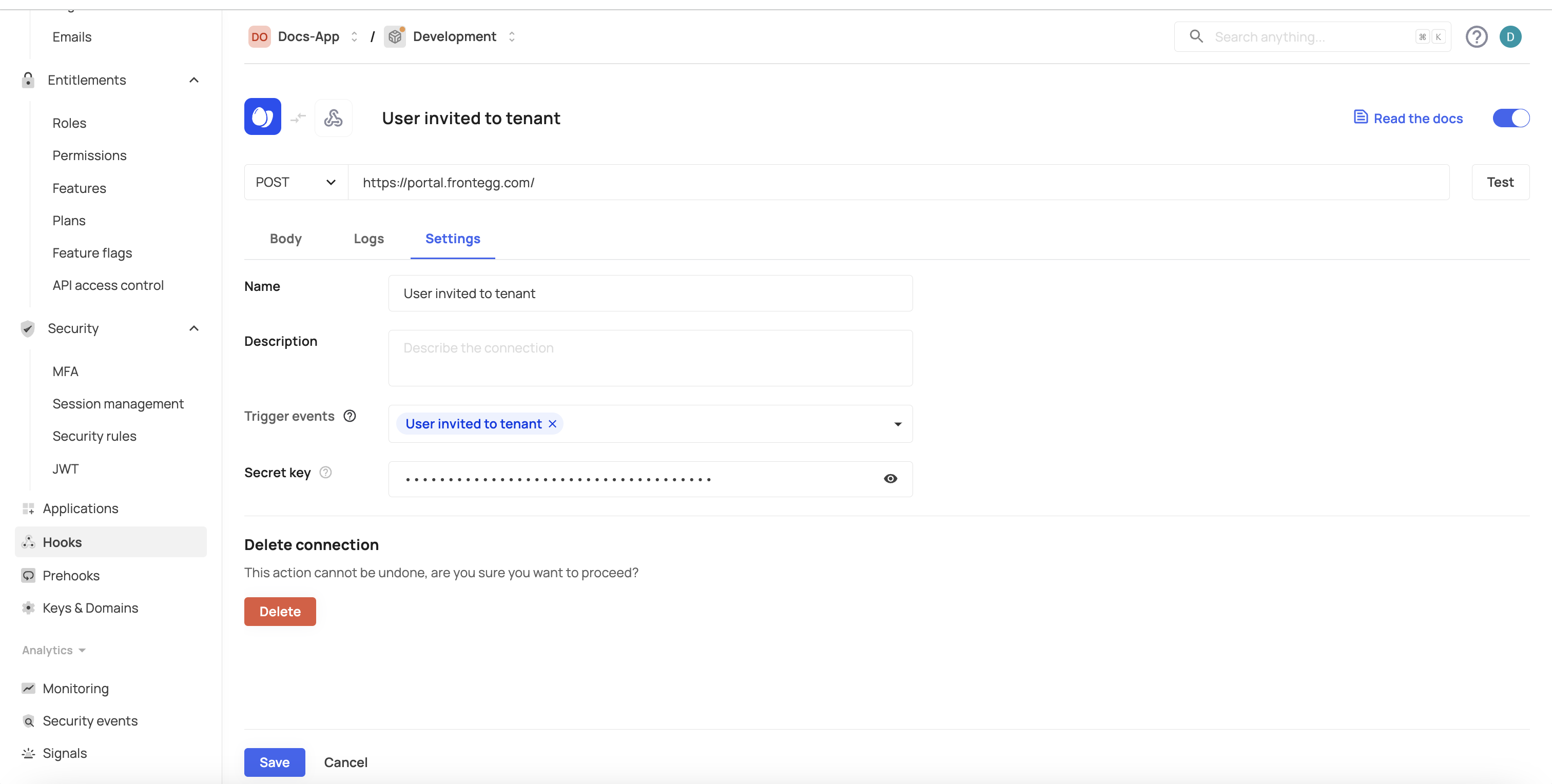
Webhook events
Webhooks in Frontegg cover multiple event types. Here's a list divided by categories:
Authentication events
| Event | Event Key | When do we send it? |
|---|---|---|
| User authenticated | frontegg.user.authenticated | a user is authenticated |
| User SAML authentication | frontegg.user.authenticatedWithSAML | a user is authenticated using SAML |
| User SSO authentication | frontegg.user.authenticatedWithSSO | a user is authenticated using SSO |
| User failed to authenticate | frontegg.user.failedAuthentication | a user tries to sign in and inputs incorrect credentials |
MFA events
| Event | Event Key | When do we send it? |
|---|---|---|
| User MFA enroll | frontegg.user.enrolledMFA | a user enrolls with MFA |
| User disabled MFA | frontegg.user.disabledMFA | a user disables MFA |
Account management events
| Event | Event Key | When do we send it? |
|---|---|---|
| Group created | frontegg.group.created | a new group is created |
| Group deleted | frontegg.group.deleted | a group was deleted |
| Group roles updated | frontegg.group.roles.updated | group roles were updated |
| Group updated | frontegg.group.updated | existing group was updated |
| Group users added | frontegg.group.users.added | new group users added |
| Group users removed | frontegg.group.users.removed | users removed from group |
| Domain restricted | frontegg.account.security.domain.restricted | domain is forbidden from signing up |
User management events
| Event | Event Key | When do we send it? |
|---|---|---|
| User created | frontegg.user.created | a user is created |
| User signed up | frontegg.user.signedUp | a user signs up |
| User deleted | frontegg.user.deleted | a user is deleted |
| User invited to tenant | frontegg.user.invitedToTenant | a user is invited to tenant |
| User changed password | frontegg.user.changedPassword | a user changes their password |
| User forgot password | frontegg.user.forgotPassword | a user forgets their password |
| User removed from tenant | frontegg.user.removedFromTenant | a user is removed from tenant |
| User API token created | frontegg.userApiToken.created | a user API token is created |
| User API token deleted | frontegg.userApiToken.deleted | a user API token is deleted |
| User activated | frontegg.user.activated | a user activates their account |
| User authenticated | frontegg.user.authenticated | a user is authenticated |
| User SAML authentication | frontegg.user.authenticatedWithSAML | user authenticated using SAML |
| User SSO authentication | frontegg.user.authenticatedWithSSO | user authenticated using SSO |
| User disabled MFA | frontegg.user.disabledMFA | user adisabled MFA |
| user MFA enroll | frontegg.user.enrolledMFA | user enrolled in MFA |
| user failed authentication | frontegg.user.failedAuthentication | unsuccessful authentication attempt |
| user joined a tenant using an invitation link | frontegg.user.joinedTenantUsingInvitationLink | User joined a tenant using an invitation link |
| temporary access edited | frontegg.user.temporary.access.edited | temporary access was edited for user |
| temporary access given | frontegg.user.temporary.access.given | access was given to a temporary user |
| Temporary user changed to permanent | frontegg.user.temporary.access.temporary.to.permanentd | temporary user changed to permanent |
| User updated | frontegg.user.updated | User profile has been updated |
Tenant events
| Event | Event Key | When do we send it? |
|---|---|---|
| Tenant created | frontegg.tenant.created | a tenant is created |
| Tenant deleted | frontegg.tenant.deleted | a tenant is deleted |
| Tenant updated | frontegg.tenant.updated | a tenant is updated |
| Tenant API token created | frontegg.tenantApiToken.created | a tenant API token is created |
| Tenant APi token deleted | frontegg.tenantApiToken.deleted | a tenant API token is deleted |
Custom webhooks
Frontegg lets you customize your webhooks, providing a more flexible and powerful way to create integrations with third-party tools. With custom webhooks, you can send data in real-time to external applications, allowing you to create customized workflows that cater to your specific needs and automate repetitive tasks. Learn more about creating Custom Webhooks
Configure webhooks in your self-service portal
You need to toggle on that option to enable webhook management for your users in the self-service portal. The toggle is located on the left, as seen in the screenshot below: