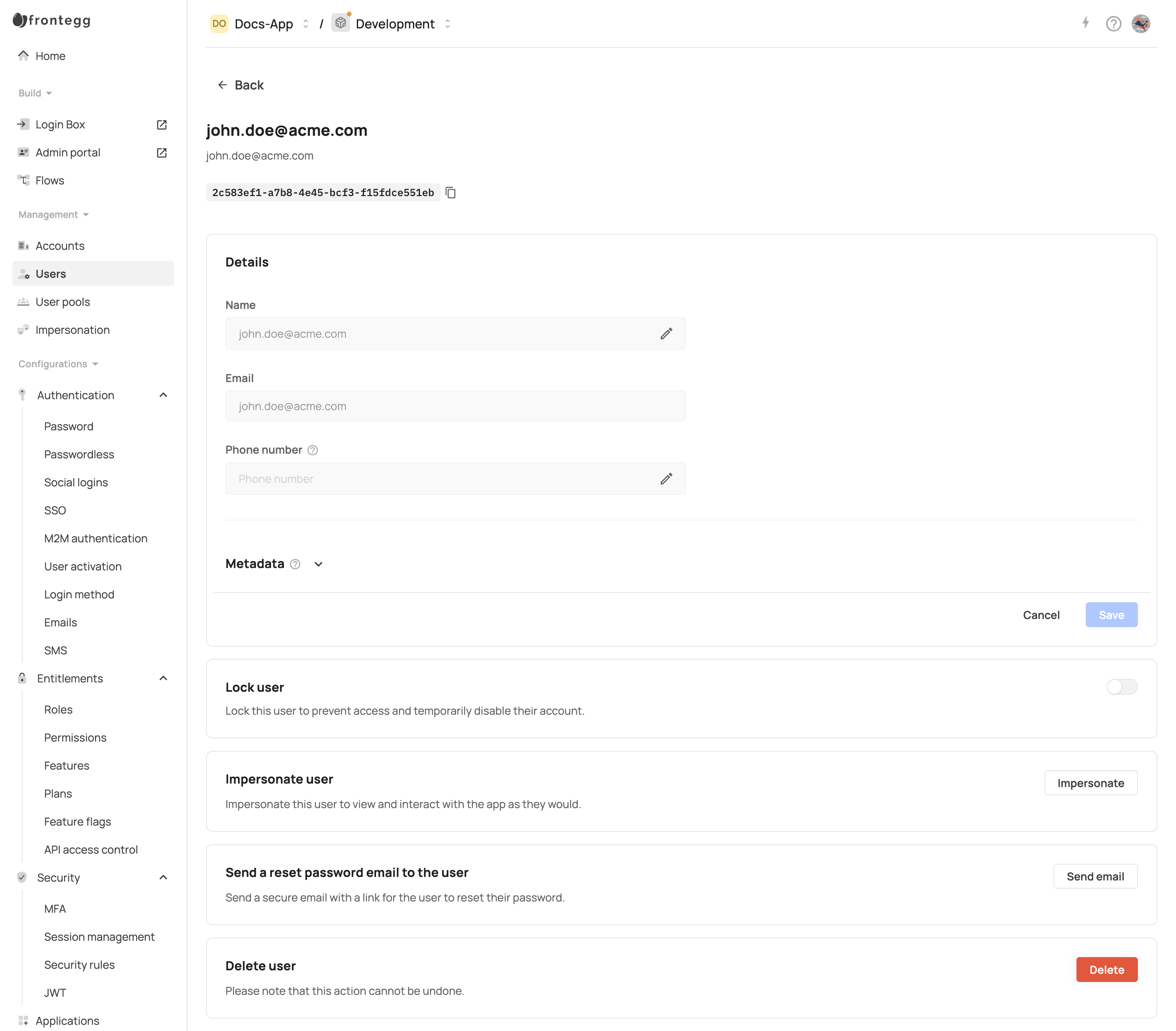
Manage users in Frontegg
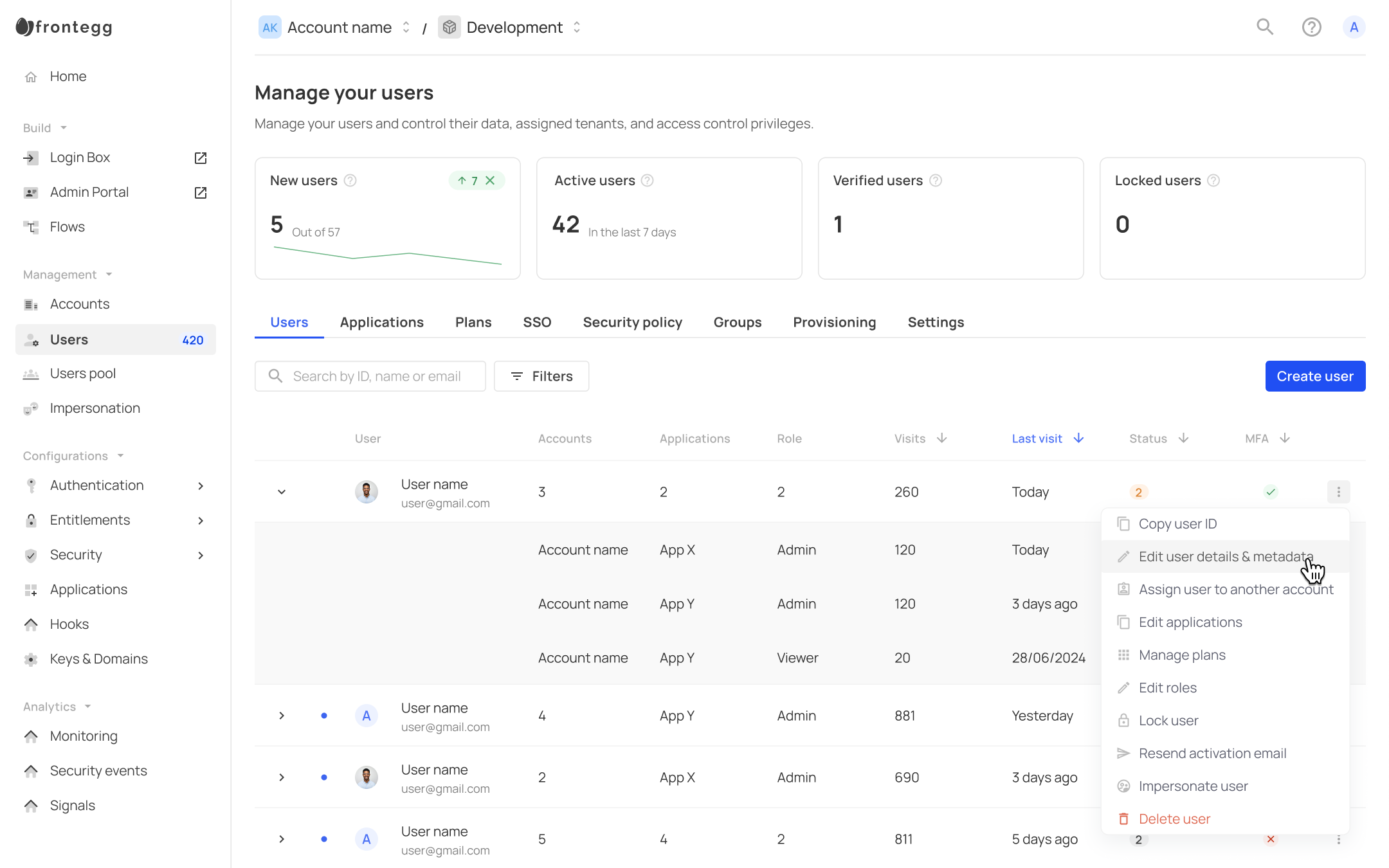
The users section under management in the Frontegg portal serves as a comprehensive user dashboard, allowing you to view and filter users across all accounts. The dashboard provides key insights, such as the number of new and active accounts, company domains, and other essential KPIs. You can also easily create new users and migrate them in bulk via the Migrations tab.
Each user entry in the table includes details about their accounts, applications, roles, verification status (whether they've confirmed their invitation via email), and whether they're enrolled in MFA.
Users analytics
Users analytics
- The Last Visit column indicates the last time a user logged into the account.
- The Visits column indicates the total visits since the account was created. If a user visits multiple times on the same day, it is counted as only one visit. This value updates daily.
Multi-tenancy by design
Frontegg is built with a multi-tenant architecture, commonly used in B2B environments, allowing users to belong to multiple accounts (tenants). This structure enables organizations to create clear segregation between teams or departments. When a user logs in and a JWT is generated, the tenantIds for the accounts they belong to are included in the token.
To implement account switching using Frontegg’s client-side SDKs, please refer to the instructions here.
Merging users based on email
The main user identifier in Frontegg is email and when users login to your application using different login methods, i.e., for example, password and social login, Frontegg will merge the user automatically.
Merging users
Merging users
If email verification is not enabled in the environment and the user's email has never been verified, they will be required to reset their password if they initially log in using a social login method and later attempt to log in with a password. This is done to enhance security.
User and vendor metadata
You can manage your users' details and metadata in two ways:
- Navigate to [ENVIRONMENT] → Management → User page
- Or use the three dots menu on the right side of each user entry for quick actions

Secure user metadata - vendorMetadata
This field is designed to store sensitive, internal data within the user object. Key characteristics:
- Not included in the user's JWT (for security)
- Typically used to store values like an internal user ID
- Useful when migrating users into Frontegg, since Frontegg generates its own user ID
See the Prehooks and metadata section below for more guidance on using this field.
User session metadata - metadata
This field stores data required during the authentication process. Key characteristics:
- Stored within the user's JWT
- Should be kept minimal to avoid performance issues with API requests that include user's access token in the headers
More on user attributes
Syncing and Customization: User attributes in Frontegg can be synchronized from external user pools, such as Auth0, Firebase, or Cognito. The synchronization ensures that user details are updated upon each login, which is particularly useful when user details are stored externally. Attributes that can be synchronized include email, name, and tenantId, and metadata.
Custom Attributes: Frontegg supports custom user attributes, which can be passed from identity providers like Okta SSO. These attributes can be configured to include various user details, enhancing the flexibility of user data management.
Prehooks and Metadata: Prehooks can be used to modify user attributes during events like user signup or invitation. This allows for customization of user data before it is stored or used in applications.
Bulk migration: For migrations, the
vendorMetadatacan be set during the migration process using the bulk migrate API, which now supports the addition of vendor metadata. This ensures that the information included in the migration remains immutable (i.e., cannot be modified) across all types of migrations. This allows you to retain internal information, identifiers, and existing application logic, ensuring a smooth and efficient migration process.UI metadata editing: In addition to programmatic options, metadata can now also be viewed and edited directly in the Frontegg dashboard through the new Single User Page.
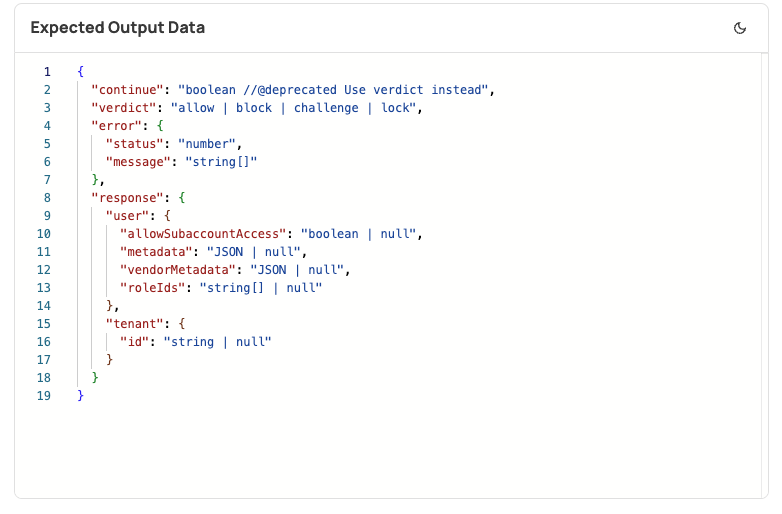
Returning secure user metadata (vendorMetadata) in the users JWT
Should you wish to return the secure user metadata (vendorMetadata) in the user's JWT, this would be your flow:
- Create a sign-up prehook, and return the
vendorMetadataas indicated in this screenshot:
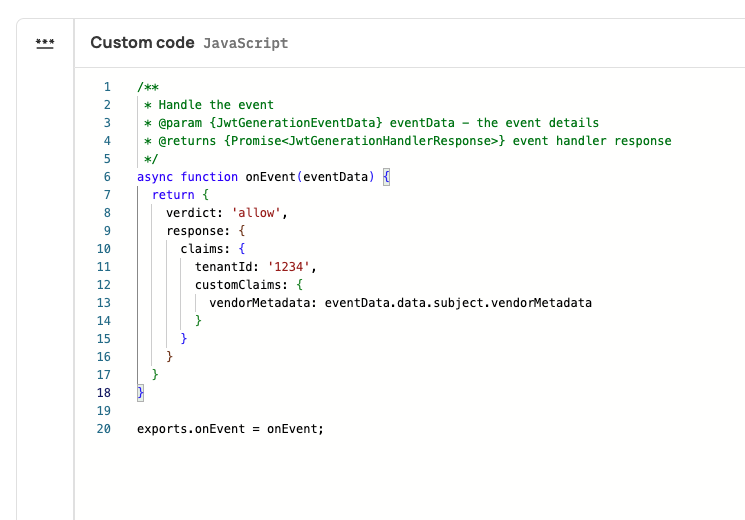
- Create a JWT Prehook To add a
vendorMetadatato the user's JWT, take it from the event data, and pass it as a custom claim, as shown here:
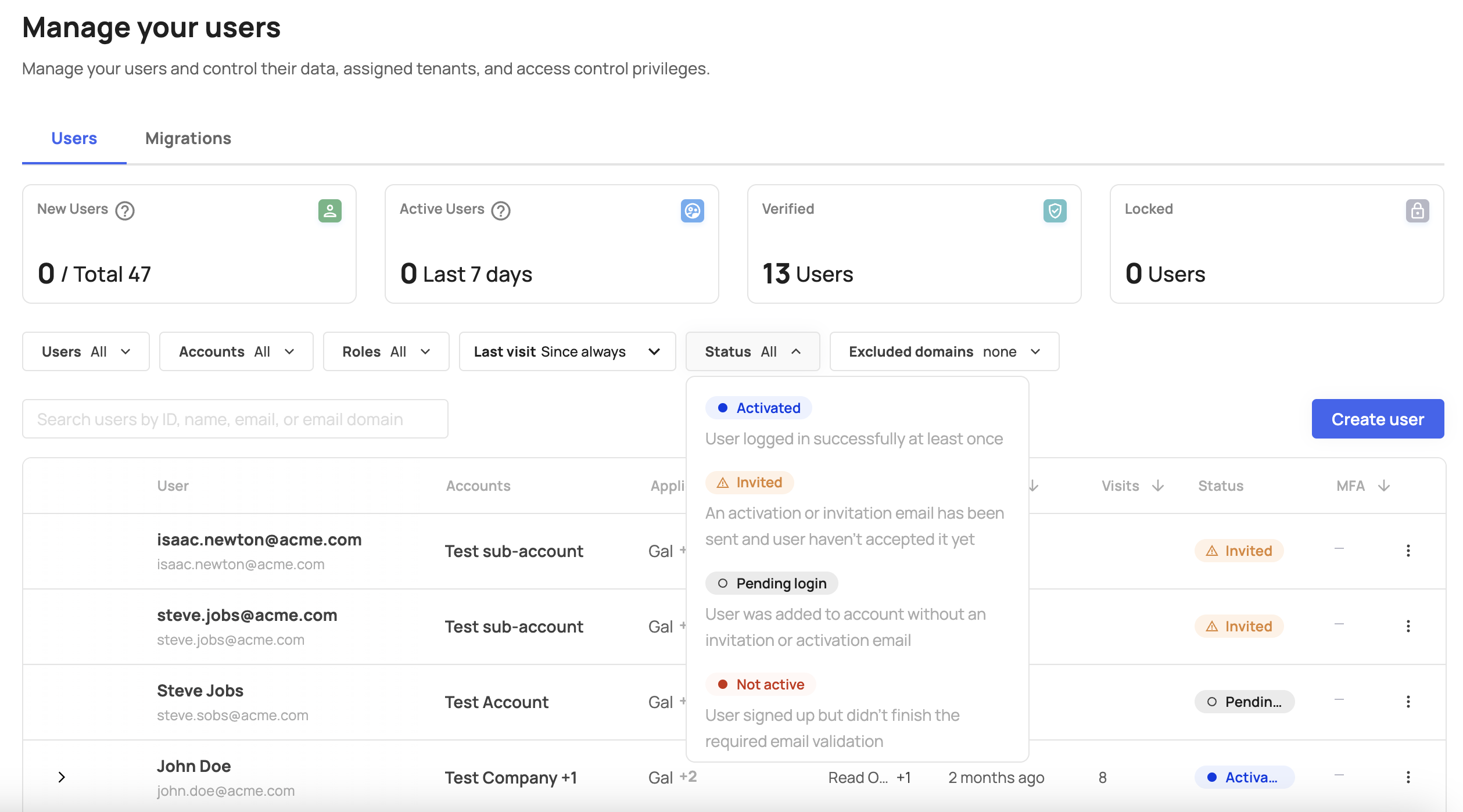
User statuses
The user management section allows filtering users using 4 main statuses:
Activated - This status does not necessarily mean that the user has clicked on the activation link sent within the activation email. The user will be marked as Activated if they logged in to the application at least once. If email verification is not required in the environment, or if the main login method is a magic link/code, the user won't necessarily need to accept the activation link in the email to be able to log in.
Invited - This status means that an activation or invitation email was sent to the user, and they must accept it in order to be added to the account.
Pending login - This status means that a user was added silently to a new account, without receiving an invitation or activation email. If a user already existed in the environment, they would just need to log in to the application. If the user did not exist before, they may need to set a password, if this is the main authentication method.
Not active - This status indicates that [email verification] is enabled in the environment, and a user has completed the sign-up form, but has accepted the activation email and hence did not verify their email address.
User searches
The management panel in the Frontegg portal allows you to search users using their name, email, or ID. However, additional search capabilities are available via APIs - Get users and Get users with fuzzy search. Note that you can perform extensive search capabilities via API, allowing you to perform both exact and fuzzy searches of user fields such as name, email, metadata, ID, and more. Whether you’re looking for partial matches or precise results, this functionality allows you to implement custom user searches tailored to your application’s needs.
Locking users via the User page
You can now lock or unlock a user directly from the User page in the Frontegg dashboard. This feature gives admins more control over individual user access without needing to disable their account entirely.
To lock a user:
- Navigate to Management → Users.
- Click on a specific user to open the Single User Page.
- In the Lock user section, toggle the switch.
- Confirm the action in the modal that appears.
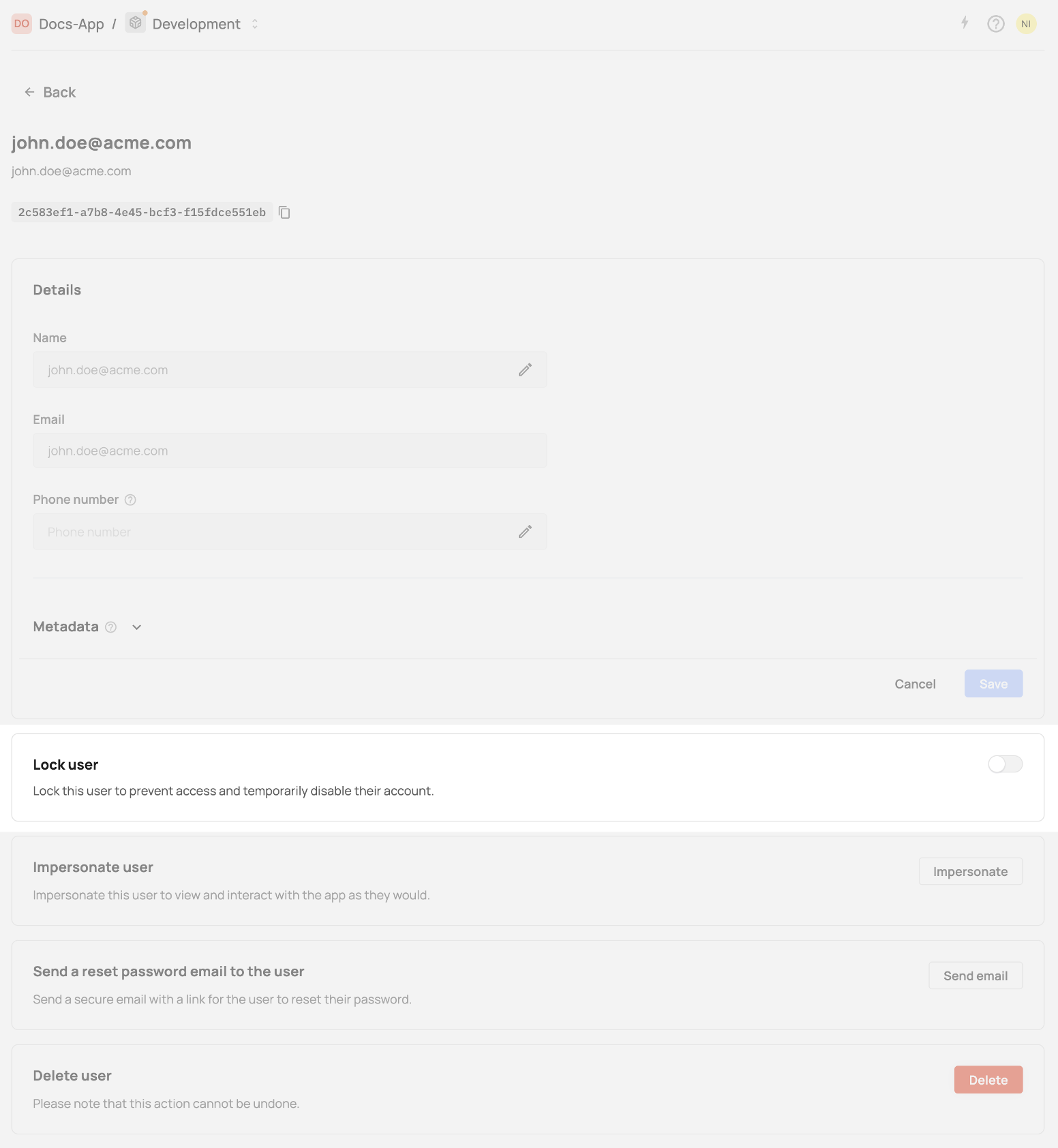
Once locked, the user will no longer be able to log in to the application. A visual "Locked" chip indicator will appear in the user's header area for quick identification.
To unlock the user, simply toggle the switch again and confirm.
Locking users
Locking users
Locking a user does not delete any of their data or remove them from accounts. It only prevents login until manually unlocked.