Authentication basics
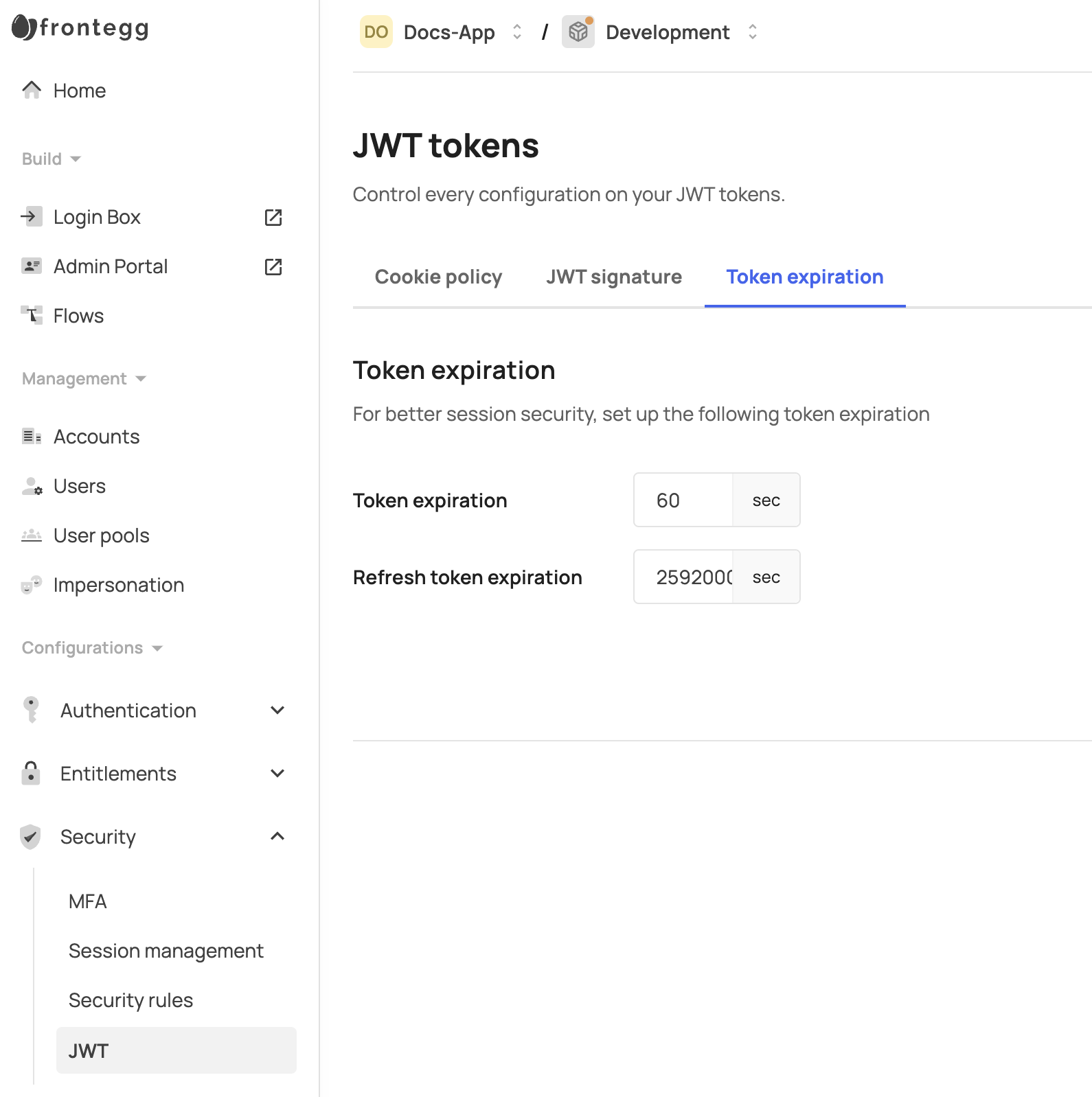
Frontegg relies on a user's access token (JWT) containing details such as the user, session ID, and application ID, along with a refresh token and cookie to renew the JWT. Since JWTs are typically invalidated only upon expiration, it is recommended to configure the JWT expiration to a maximum of a few minutes in the JWT section of your environment for enhanced security.
Token types
Token types
Note that these settings control the expiration of all JWTs, including those that are created for client credentials tokens.
Refreshing JWT tokens
When using Frontegg's client-side (web) SDKs with short-lived JWTs, enable the keepSessionAlive:true flag to refresh the user's access token (JWT) in the background, this will prevent automatic logout when the user's JWT expires. This flag will automatically calculate 80% from the JWT expiration and will refresh it, using the refresh token or cookie.
JWT modifications
Keep in mind that a user's JWT claims contain their permissions, accounts, and metadata, but it is also included in request headers, which are often limited to 8K or, in some cases, 16K characters. Adding excessive permissions or large metadata objects may impact authentication and lead to failures. To mitigate this, consider removing roles or permissions from JWTs when necessary. This can be done via this API.
Additional claims, may be added via JWT generation prehook and propagated into the JWT as custom claims.
JWT expiration
As noted above, the Token expiration setting controls the expiration time for all tokens, including JWTs generated for personal or API tokens (client credentials). If different expiration times are needed for specific token types—such as user tokens and client credentials tokens—the expiresIn attribute can be used to specify these durations, as returned in the JWT generation prehook.
Refresh tokens rotation
By default, Frontegg rotates refresh tokens, meaning each token can be used only once and is invalidated after use. However, certain flows or implementations may require disabling token rotation to allow reusing the same refresh token multiple times. This can be achieved, by passing rotateRefreshTokens:false to this API.