AI Agents with Frontegg Entitlements
AI agents often act autonomously on behalf of users, executing actions like updating tickets, posting messages, or pulling reports. To ensure every action is authorized according to your business logic, Frontegg provides a native integration between its Entitlements Engine and AI Agents using MCP tools.
This guide covers:
- Deploying the Entitlements Agent (with MCP support)
- Connecting your AI agent to MCP tools
- Enforcing policy checks autonomously through prompt engineering
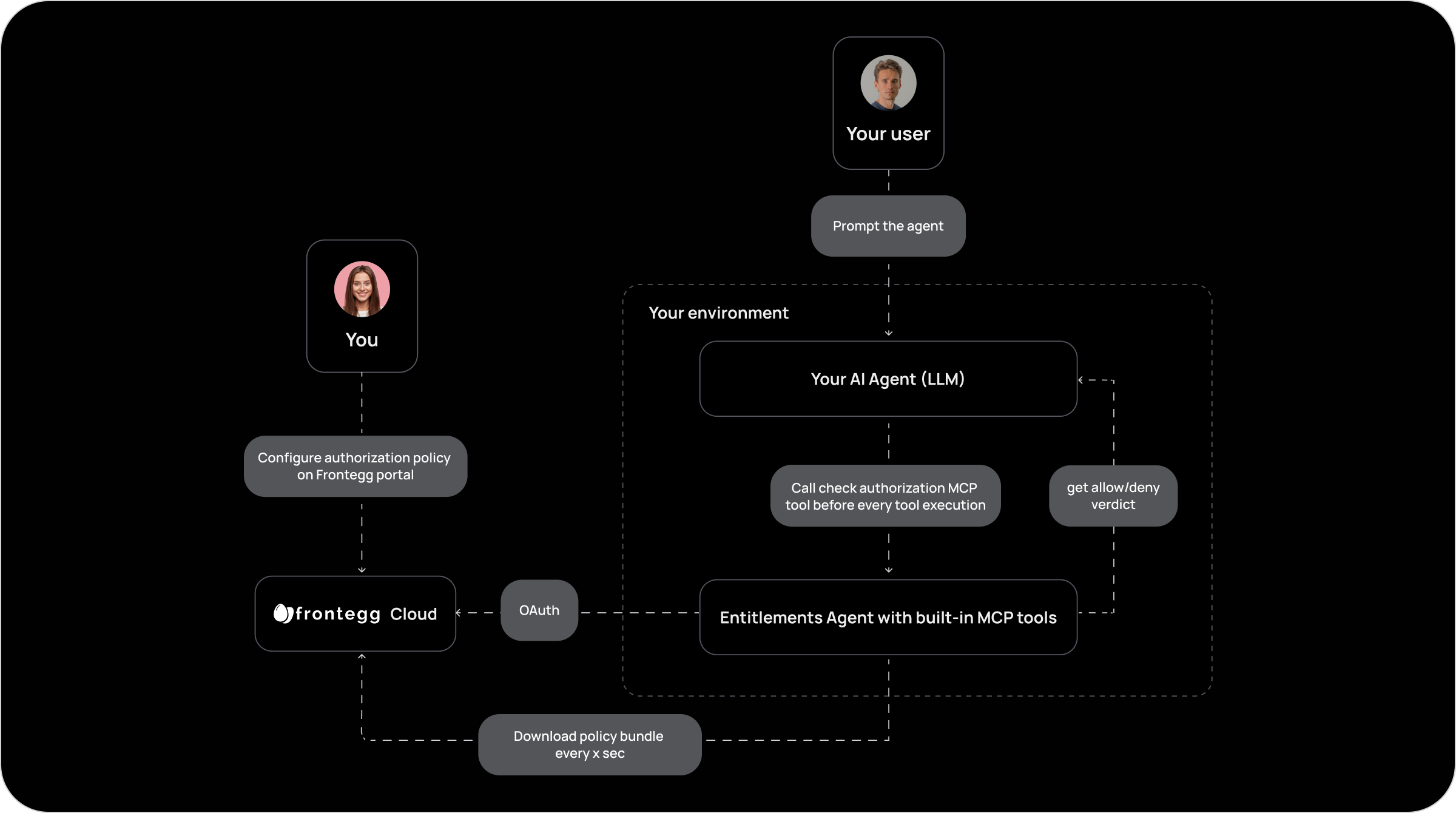
Step 1: Deploy the Entitlements Agent with MCP
Start deploying the Entitlements Agent in your environment using Helm with custom values.yaml configuration file:
- Create
values.yaml
In order to obtain fronteggClientCredentialsOauthClientId and fronteggClientCredentialsOauthSecret, please follow these instructions.
env:
# PDP Agent container environment variables
pdpAgent:
fronteggRegion: "eu" / "us" / "ca" / "au"
fronteggClientId: "FRONTEGG_CLIENT_ID"
fronteggClientCredentialsOauthClientId: "FRONTEGG_CLIENT_CREDENTIALS_OAUTH_CLIENT_ID"
fronteggClientCredentialsOauthSecret: "FRONTEGG_CLIENT_CREDENTIALS_OAUTH_SECRET"
pollingMinDelay: "30"
pollingMaxDelay: "60"
# MCP Server container environment variables
mcpServer:
pdpUrl: "http://localhost:8181"- Install using Helm
helm repo add frontegg https://frontegg.github.io/helm-charts
helm repo update
helm install entitlements-agent frontegg/entitlements-agent --values values.yamlThis deploys:
- The Entitlements Agent (PDP) – fetches and syncs policies from Frontegg
- An MCP Server – exposes authorization tools over HTTP for local access by your agent
Step 2: Connect your AI Agent to MCP
You can now connect your AI Agent to the MCP server to access the entitlement tools programmatically.
Example (TypeScript):
import { Client, StreamableHTTPClientTransport, loadMcpTools } from 'mcp-sdk';
const entitlementsMcpClient = new Client({
name: 'ent',
version: '1.0.0',
serverUrl: 'http://127.0.0.1:8182/mcp', //this is the MCP server URL deployed in the helm chart before
});
await entitlementsMcpClient.connect(
new StreamableHTTPClientTransport(new URL('http://127.0.0.1:8182/mcp'))
);
const entitlementsTools = await loadMcpTools('entitlements', entitlementsMcpClient);Available MCP tools
After connecting, your agent can use the following tools:
| Tool Name | Description |
|---|---|
| is-entitled-to-entity-action-tool | Performs an entitlement check for a given user/entity and requested action. |
| entitlements-entities-tool | Returns a list of entity types and actions available in the current policy. |
Step 3: Enforce Authorization Using Prompt Instructions
To ensure your agent performs checks before any operation, provide it with the following system prompt:
Important! oauth tools do not require an action, you can execute them directly.
Important! before executing any tool other than the oauth* tools, verify the tool is allowed by executing the 'is-entitled-to-entity-action-tool' using the user ID from the context and the entities from the 'entitlements-entities-tool'.
Important! before executing the 'is-entitled-to-entity-action-tool', you must call the 'entitlements-entities-tool' MCP tool.
The default entityType of the executing entity when using entitlements is 'user'.This makes the AI agent:
- Call entitlements-entities-tool first to discover the available schema
- Use the is-entitled-to-entity-action-tool before executing any action
- Enforce policy autonomously, without relying on backend API enforcement
Summary
| Capability | Description |
|---|---|
| Policy sync | Policies are pulled periodically from Frontegg to your environment |
| Local enforcement via MCP | AI agents check authorization before action using MCP tools |
| Agent-autonomous access control | Prompts instruct the agent to verify entitlement without app-side logic |
By combining Frontegg Entitlements with MCP tooling, AI agents become secure, policy-aware entities that enforce authorization with no developer intervention required per action.