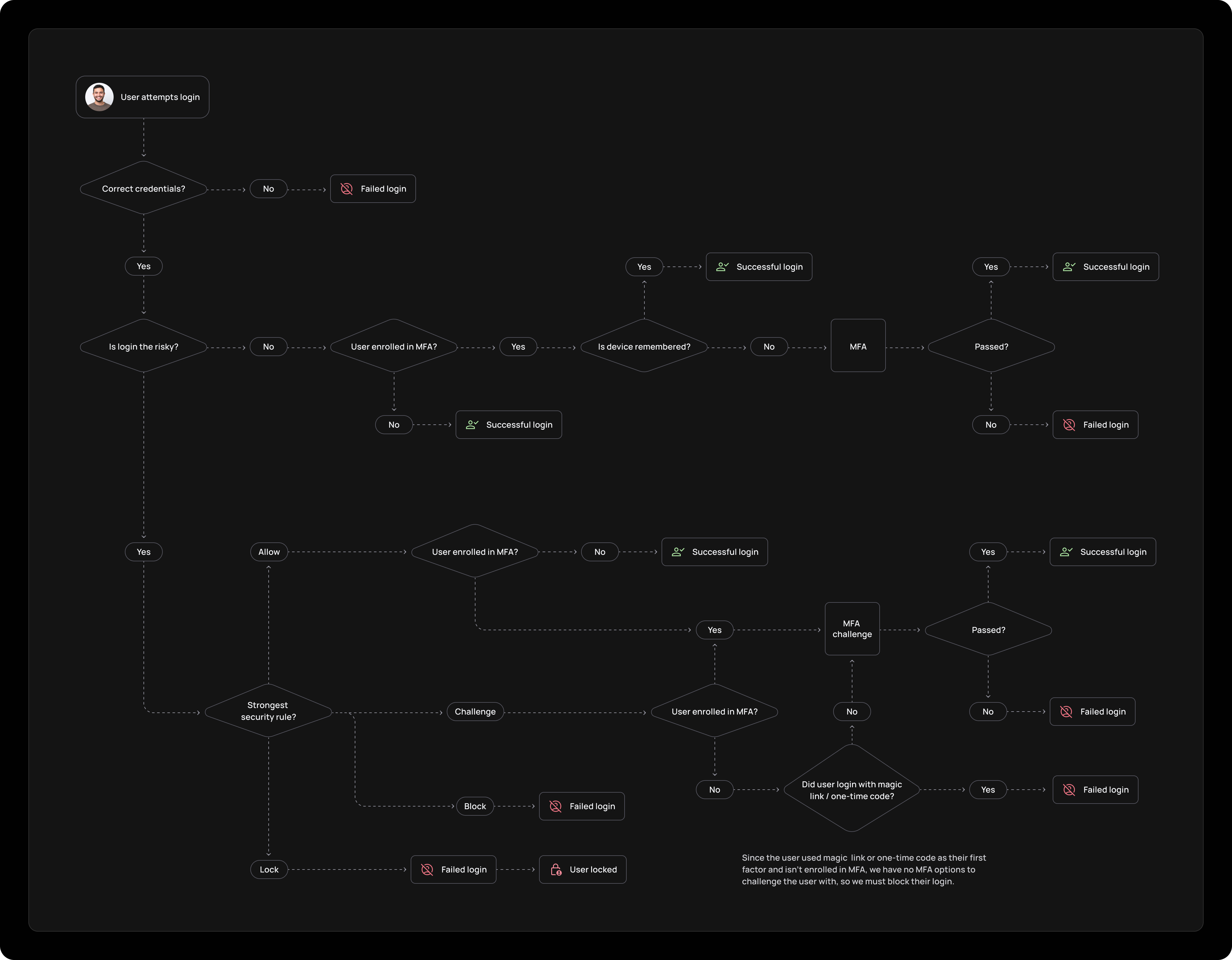
Frontegg provides 8 built-in security defenses, each configurable with different actions when triggered. For example, you can allow inactive users to continue using your app but block them if they attempt to use a compromised password.
| Defense | Description | Allow | Challenge | Block | Lock |
|---|---|---|---|---|---|
| Bot detection | Identifies malicious bots to prevent security threats | ✓ | ✓ | ✓ | ✓ |
| New device | Analyzes device characteristics to detect potential security threats | ✓ | ✓ | ||
| Brute force protection | Detects repeated failed login attempts to prevent unauthorized access | ✓ | ✓ | ||
| Breached password | Blocks use of passwords known to be compromised in data breaches | ✓ | ✓ | ✓ | |
| Impossible travel | Detects logins from different locations within an unreasonably short timeframe | ✓ | ✓ | ✓ | |
| Suspicious IPs | Identifies suspicious IP activity, allowing detection or prevention of threats | ✓ | ✓ | ✓ | ✓ |
| Stale users | Deactivates inactive accounts to reduce security risks | ✓ | ✓ | ✓ | |
| Email credibility check | Allows only validated emails with good reputations at sign-up | ✓ | ✓ |
To modify policies for any defense that Frontegg offers, users with an Admin role in the Frontegg account can access and adjust settings from the Security Rules page within any environment.