Data Protection in AgentLink allows you to identify and mask sensitive information (such as PII, PHI, or PCI) in tool responses before they are returned to AI agents.
This ensures your organization stays compliant with privacy and security regulations like GDPR, HIPAA, and CCPA while maintaining full AI functionality.
When an AI agent executes a tool, AgentLink automatically inspects the response payload.
If the response contains fields that match your defined data protection policies, those values are masked or replaced before being returned to the agent.
You can define one or more policies that specify:
- What types of data to protect (e.g., emails, SSNs, health records)
- Which tools to apply the masking to
- Optional conditions that determine when masking should occur
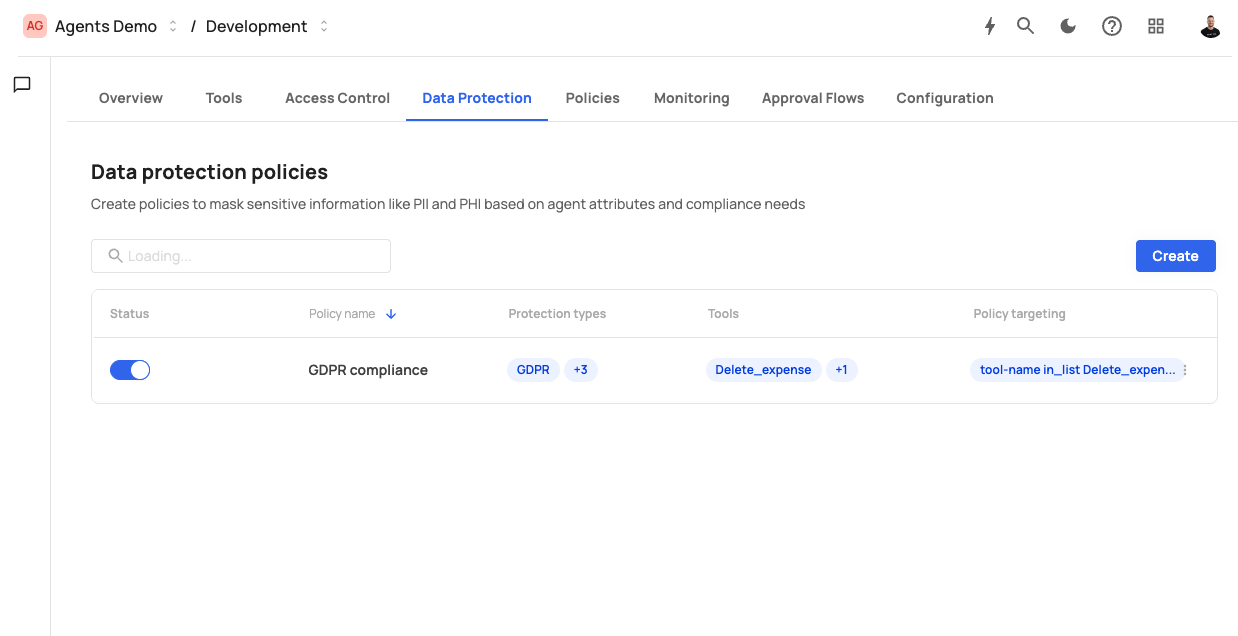
The Data Protection page lists all masking policies currently active in your MCP server.
Table columns
- Status — Indicates whether the policy is active or disabled.
- Name — The name of the masking policy.
- Protected Tools — The tools this policy applies to.
- Protection Types — Which compliance groups (GDPR, PCI, PHI, etc.) are included.
- Applications — Number of MCP applications using the policy.
- Conditions — Optional conditions that trigger masking (e.g., user role ≠ admin).
- Created — When the policy was created.
Click Create to add a new masking policy.
To create a new data protection policy:
- Click Create on the top-right corner of the Data Protection screen.
- In the dialog, fill in the following fields:
- Policy name — A clear, descriptive name (e.g., “Mask Customer PII”).
- Description — Describe what this policy protects and why.
- Data types to protect — Choose from predefined compliance frameworks or specific fields (see Masking Types).
- Tools — Select which tools the masking applies to.
- Policy targeting — Define optional conditions that determine when masking is enforced.
- You can target based on user roles, departments, or request context.
- Examples:
user.role != admin— Mask data for all users except admins.request.context == external_api— Mask data only when accessed externally.user.department != finance— Mask finance data for non-finance users.
- Click Create to save the policy.
Once saved, the policy is active immediately when enabled.
Each policy has an on/off switch in the Status column.
- Enabled: Masking is active and enforced for selected tools.
- Disabled: The policy remains stored but is ignored by the system.
You can toggle the switch at any time without deleting the policy.
A finance company wants to hide personal identifiers in its “Delete_expense” tool responses.
| Setting | Example |
|---|---|
| Policy name | GDPR Compliance |
| Data types | Email address, Bank number, Phone number |
| Tools | Delete_expense |
| Protection type | GDPR |
| Condition | user.role != admin |
When a non-admin agent calls the Delete_expense tool, AgentLink masks all detected personal identifiers.
AgentLink provides pre-built sets of data types aligned with global standards:
| Framework | Example Data Types |
|---|---|
| GDPR | Email, Phone, Bank Account, Passport Number |
| PHI (HIPAA) | Medical License, Health Record IDs |
| PCI DSS | Credit Card Number, CVV |
| CCPA | SSN, Driver License, Address |
| COPPA | Child Name, Birth Date |
You can mix and match data categories or select all fields under a framework.
To confirm your masking policy works correctly:
- Run or simulate a tool that returns protected data.
- Verify the masked fields in the response (e.g.,
"email": "***@***.com"). - Review logs in the Monitoring screen for masked-value indicators.
- Create separate policies for each compliance framework (e.g., GDPR, PCI).
- Keep policies scoped to only relevant tools to avoid unnecessary masking.
- Review masked outputs regularly to ensure data accuracy.
- Combine with Policies & Guardrails for conditional masking and approvals.