Forwarding client IP for security rules and rate limits
When using Next.js with Frontegg authentication, security rules and rate limits typically rely on the server’s IP address instead of the actual client’s IP. This can cause issues when enforcing authentication methods such as Multi-Factor Authentication (MFA), SMS-based verification, or rate limiting.
To ensure that Frontegg receives the correct client IP, add the following features to your .env.local file:
FRONTEGG_FORWARD_IP=true
FRONTEGG_SHARED_SECRET=your-shared-secret-hereFeature activation required
Feature activation required
This feature must be enabled for your environment by the Frontegg team. To request activation, contact support.
Prerequisites
Prerequisites
@frontegg/nextjs@9.2.2
The shared secret is a security key used to secure your requests to Frontegg. You can retrieve it in one of the following ways:
Option 1: From the Frontegg portal
- Go to Configurations → Applications
- Select or create a Next.js application
- Scroll down to the Shared secret section
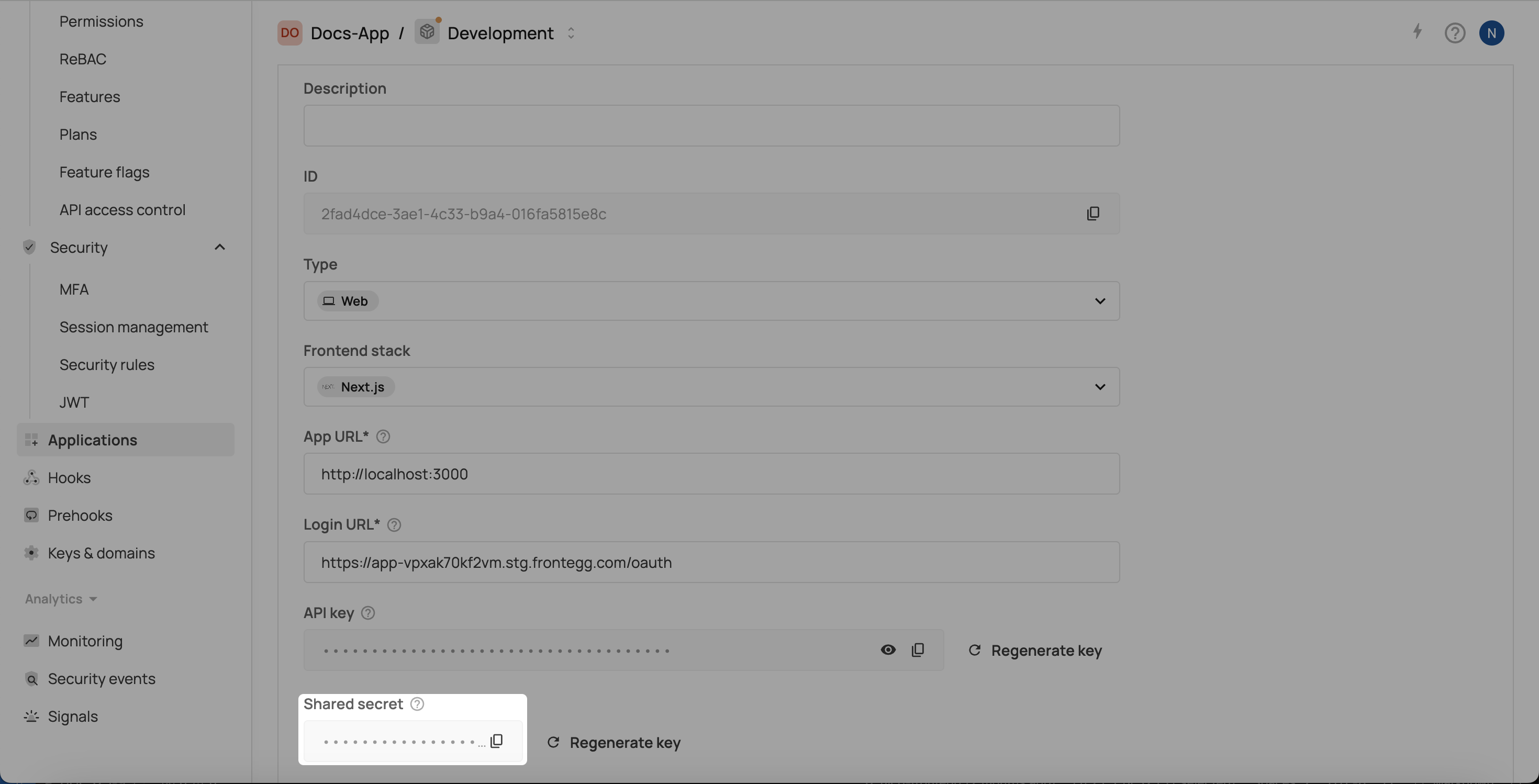
Option 2: Using the API
Make a GET request to the Get Application Client Credentials API using your environment token.