Machine-to-machine tokens
Frontegg Machine-to-Machine (M2M) tokens are used for authentication and authorization, granting users access to specific resources in your app.
M2M tokens, often referred to as Access Tokens, are commonly utilized in OAuth authentication flows. These flows allow users to grant permission to third-party applications to access their resources without sharing sensitive credentials. Compared to session tokens, M2M tokens are more flexible and less sensitive, making them suitable for longer validity periods. Access Tokens act as bearer tokens, providing the necessary credentials to access protected resources.
Passing Token Bearers
Passing Token Bearers
When using an Access Token, the token bearer must be passed in the X-API-KEY header.
For Client Credentials Tokens, the token bearer must be passed in the Authorization header.
Enabling token generation for users
Frontegg supports two types of Machine-to-Machine (M2M) tokens:
- Access Tokens: Flexible tokens that can optionally have expiration periods. Ideal for third-party integrations.
- Client Credentials Tokens: Tokens designed for passwordless authentication methods, such as magic codes/links. These tokens are inherently time-sensitive.
To enable users to generate M2M tokens:
- Open the Frontegg portal.
- Navigate to [ENVIRONMENT] → Configurations ➜ Authentication → M2M authentication.
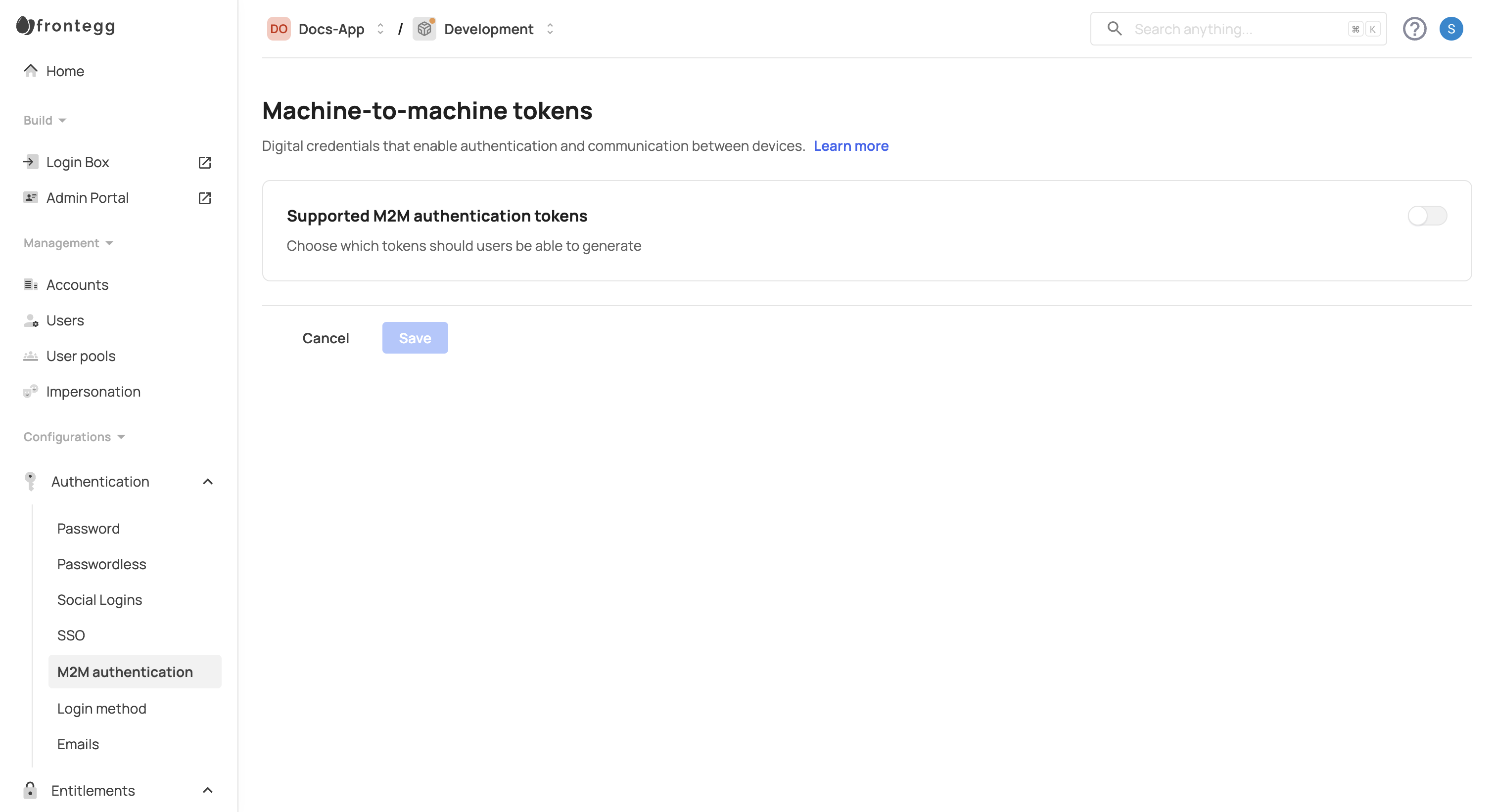
- Toggle the Supported M2M authentication tokens button to enable token generation.
- Choose the token type to enable: Access Tokens or Client Credentials Tokens.
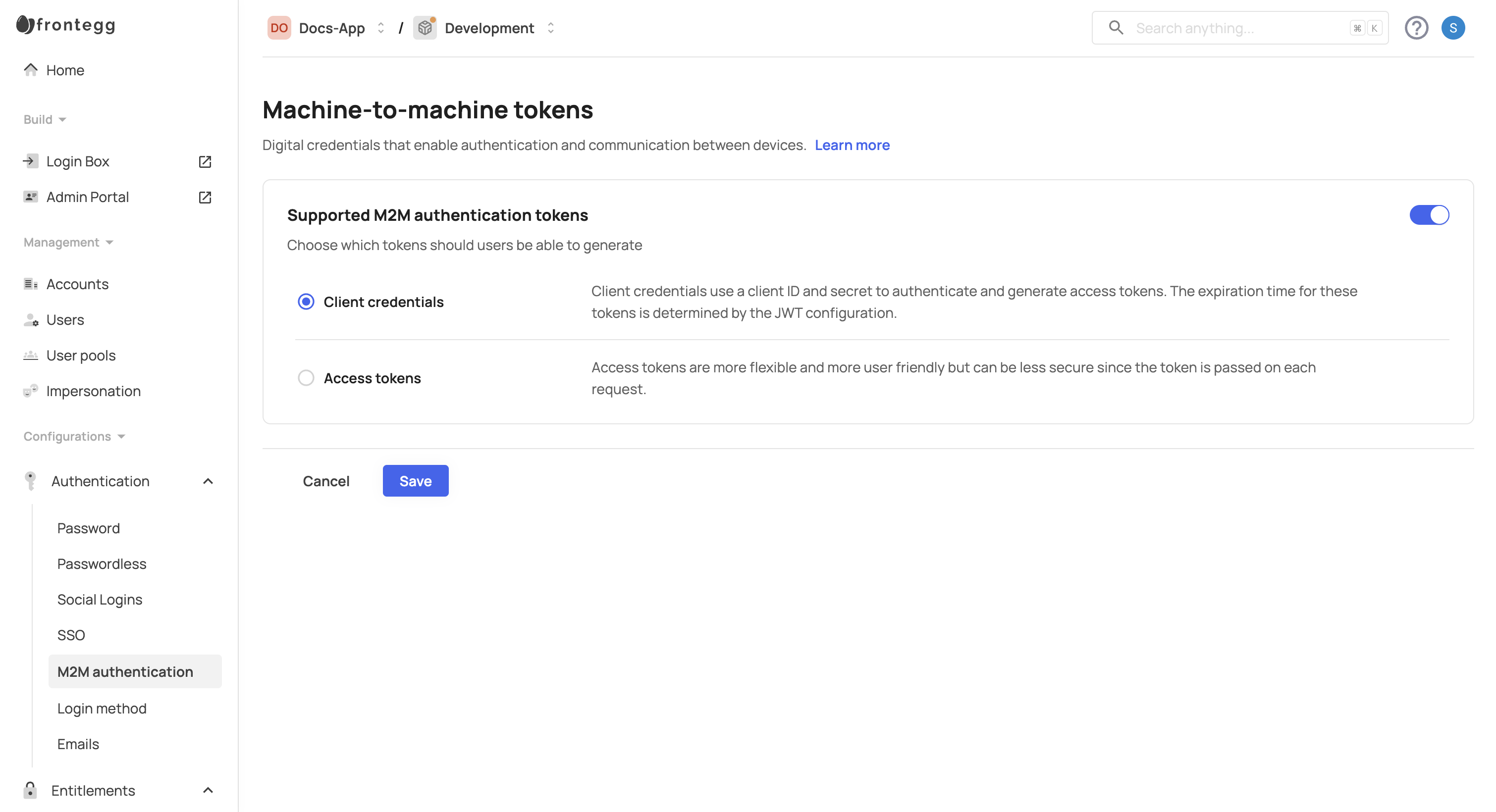
- Save your changes to allow users to generate the selected token types.
Setting expiration for M2M tokens
Both client credentials and access tokens can be set as temporary with different expiration times. Note that in the case of client credentials, there are two types of expirations to consider — the expiration of the client credentials and the expiration of the access token (JWT) generated using these credentials. The following refers to the expiration of client credentials only. JWT expiration is managed globally for the entire environment under Security → JWT.
Prerequisites
Prerequisites
To set expiration time for M2M tokens, the following versions are required:
@frontegg/react@6.0.9
@frontegg/angular@6.9.0
@frontegg/vue@3.0.9
@frontegg/nextjs@8.0.7
Managing account generated tokens in an environment
The Accounts page in the Frontegg portal provides a centralized interface for managing account-generated tokens within your environment. You can create new tokens, delete existing ones, and view tokens created by account administrators, with the option to delete them if needed — all from one convenient location.
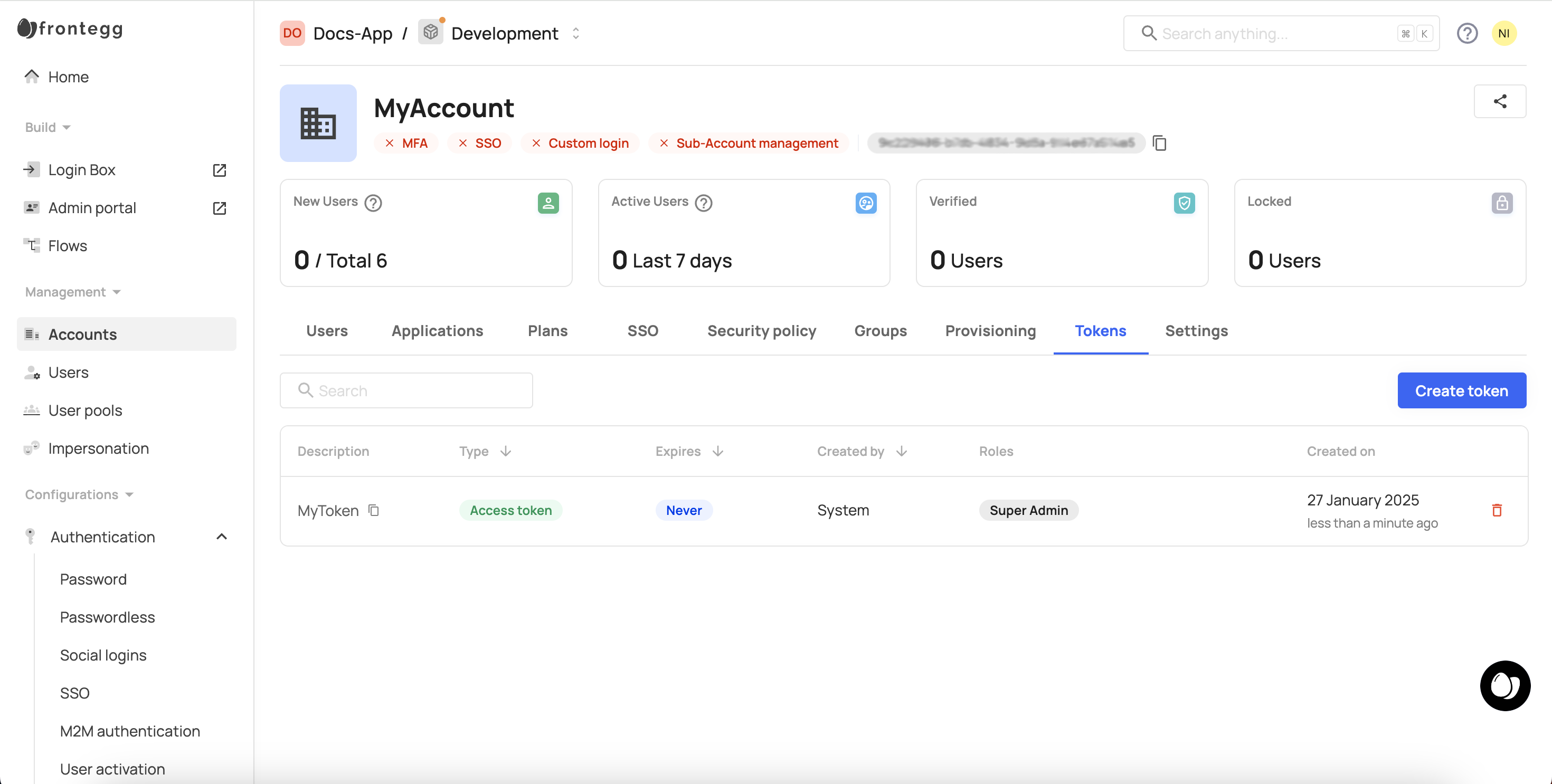
Creating account tokens in an environment
The type of token generated will depend on the Access Token type selected for the environment.
- Open the Frontegg portal.
- Navigate to [ENVIRONMENT] → Accounts.
- Select the account for which you need to generate the account token.
- Go to the Tokens tab.
- Click Create Token.
- Enter a description for the token in the Description field.
- Select the roles to assign to this token from the Roles dropdown.
- Choose the expiration time for the token from the Expiration Time dropdown.
- Click Create.
- Copy and securely save the displayed token, as it will not be shown again.
- Click Done.
Deleting account tokens in an environment
- Open the Frontegg portal.
- Navigate to [ENVIRONMENT] → Accounts.
- Select the account where you need to delete the account token.
- Go to the Tokens tab.
- Click the bin icon next to the token you want to delete.
- Click Delete Token.
Using API routes
Creating personal tokens via API
Want to experiment with API tokens before allowing your users the self-service experience they deserve? No worries — we've got you covered!
Authenticate your environment
Before performing any further actions, you need to authenticate your environment. Retrieve your Client ID and API key (secret) from the Keys & domains section in the Frontegg portal. Use these credentials to generate an environment token by referring to the environment authentication guide.
Create user token
User tokens are tied to a specific user and always include the user context, including roles and permissions assigned to the user on the active account (tenant). These tokens can be generated as either client credentials or access tokens, depending on your use case.
Client credentials for user tokens
Client credentials tokens for users provide a clientId and secret, which can be used for token exchanges, allowing you to authenticate on behalf of the user. To create a client credentials token for a user, click here.
This API will return the clientId and secret associated with the user token.
Secrets are only displayed in plain text at the time of API token creation. After that, they are securely stored using hashing and encryption methods, making them impossible to retrieve or reverse.
Access tokens for user tokens
Access tokens for users are JWTs ready for immediate use in authentication. These tokens can include an expiration time and are ideal for scenarios where you need a token for direct use. To create an access token for a user, click here.
This API will directly return the user access token, which is ready for use.
Once you have these credentials, you're all set to authenticate your API!
Creating account (tenant) tokens via API
Client credentials for account tokens
Client credentials tokens for accounts provide a clientId and secret, which can be used for token exchanges, allowing you to authenticate on behalf of the account. To create a client credentials token for an account, click here.
This API will return the clientId and secret associated with the account token.
When creating a client credentials token, you will need to include the roleIds, which define the roles associated with the token. These roles determine the permissions granted to the token and help define its scope within the account (tenant) context.
Secrets are only displayed in plain text at the time of API token creation. After that, they are securely stored using hashing and encryption methods, making them impossible to retrieve or reverse.
Access tokens for tenant tokens
Access tokens for tenants are JWTs that are ready for immediate use in authentication. These tokens can include an expiration time and are ideal for scenarios where you need a token for direct use. To create an access token for an account (tenant), click here.
This API will directly return the account access token, which is ready for use.
Similar to client credentials tokens, when creating access tokens for accounts, you must include the roleIds. This ensures that the token has the appropriate roles and permissions needed for the specific actions it will be used for.
Authenticate using API token
Use this route to authenticate an account's or user's API token, returning an access token for subsequent requests.
Learn more about the authenticate using API token API.
Refresh API token
Use this route to refresh an expired JWT using a valid refresh token, generating a new access token and refresh token.
Learn more about the refresh API token API.